Policies_VoIP_Settings_Snwls
CHAPTER 21
Configuring Voice over IP Settings
To configure Voice over IP (VoIP) settings, perform the following steps:
1. Select the global icon, a group, or a SonicWALL appliance.
2. Expand the Firewall tree and click VoIP. The VoIP page displays.
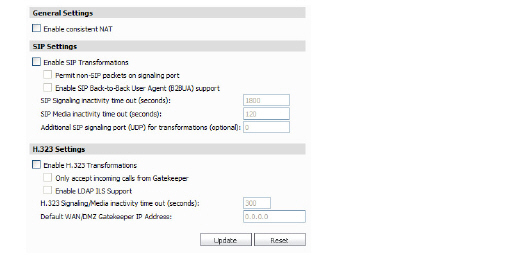
3. To enable secure NAT, select the Use secure NAT check box.
4. Select Enable SIP Transformations to support translation of Session Initiation Protocol (SIP) messages.
Tip By default, NAT translates Layer 3 addresses, but does not translate Layer 5 SIP/SDP addresses. Unless there is another NAT traversal solution that requires this feature to be turned off, it is highly recommended to enable SIP transformations.
After enabling SIP transformations, configure the following options:
a.Select Permit non-SIP packets on signaling port to enable applications such as Apple iChat and MSN Messenger, which use the SIP signaling port for additional proprietary messages. Enabling this checkbox may open your network to malicious attacks caused by malformed or invalid SIP traffic. This checkbox is disabled by default.
b.(SonicOS Enhanced only) Select the Enable SIP Back-to-Back User Agent (B2BUA) support setting when the SonicWALL security appliance can see both legs of a voice call (for example, when a phone on the LAN calls another phone on the LAN). This setting should only be enabled when the SIP Proxy Server is being used as a B2BUA.
Tip If there is not the possibility of the SonicWALL security appliance seeing both legs of voice calls (for example, when calls will only be made to and received from phones on the WAN), the Enable SIP Back-to-Back User Agent (B2BUA) support setting should be disabled to avoid unnecessary CPU usage.
– SIP Signaling inactivity time out (seconds)—Specifies the period of time that must elapse before timing out an inactive SIP session if no SIP signaling occurs (default: 1800 seconds or 30 minutes).
– SIP Media inactivity time out (seconds)—Specifies the period of time that must elapse before timing out an inactive SIP session if no media transfer activity occurs (default: 120 seconds or 2 minutes).
– The Additional SIP signaling port (UDP) for transformations setting allows you to specify a nonstandard UDP port used to carry SIP signaling traffic. Normally, SIP signaling traffic is carried on UDP port 5060. However, a number of commercial VoIP services use different ports, such as 1560. Using this setting, the security appliance performs SIP transformation on these non-standard ports.
Tip Tip: Vonage’s VoIP service uses UDP port 5061.
5. Select Enable H.323 Transformations to allow stateful H.323 protocol-aware packet content inspection and modification by the SonicWALL. The SonicWALL performs any dynamic IP address and transport port mapping within the H.323 packets, which is necessary for communication between H.323 parties in trusted and untrusted networks/zones. Clear this check box to bypass the H.323 specific processing performed by the SonicWALL.
After enabling H.323 transformations, configure the following options:
– Only accept incoming calls from Gatekeeper—when selected, only incoming calls from specified Gatekeeper IP address will be accepted.
– Enable LDAP ILS Support— when selected, the SonicWALL appliance will support Lightweight Directory Access Protocol (LDAP) and Microsoft Netmeeting’s Internet Locator Service (ILS)
– H.323 Signaling/Media inactivity time out (seconds)—specifies how long the SonicWALL appliance waits before closing a connection when no activity is occurring.
– Default WAN/DMZ Gatekeeper IP Address—specifies the IP address of the H.323 Gatekeeper that acts as a proxy server between clients on the private network and the Internet.
6. When you are finished, click Update. The settings are changed for each selected SonicWALL appliance. To clear all screen settings and start over, click Reset.