Reporting_Firewall
The Reports available under the Firewall tab provide specific information on data gathered by the Dell SonicWALL Analyzer interface.
For a general introduction to reporting, see Dell SonicWALL Analyzer Reporting Overview.
The Firewall reports display either summary or unit views of connections, bandwidth, uptime, intrusions and attacks, and SRA usage, displayed in a Data Container. Information can be viewed in either chart (timeline or pie chart) form, or tabular (grid) format. The list of available reports allows you to navigate to a high-level or specific view.
All of the reports in Analyzer report on data gathered on a specific date or range of dates. Data can be filtered by time constraints and data filters.
Benefits of Firewall Reporting
Firewall Reports allow you to access both real-time and historical reports and view all activity on SonicWALL Internet security appliances. By monitoring network access, logins, and sites accessed, you can enhance system security, monitor internet usage, and anticipate future bandwidth needs.
You can gain more information from the display, simply by hovering the mouse pointer over certain sections. Additionally, by clicking on selected sections of a pie chart or bar-graph timeline view, you can view more information or view different aspects of the information presented.
The Firewall tab gives you access to the Firewall’s reports section of the Dell SonicWALL Analyzer management interface. Reporting supports both graph and non-graph reports, and allows you to filter data according to what you wish to view. It supports multiple product-licensing models.
Firewall Reports provide the following features:
• Clickable reports with drill-down support on data rows
• Report data filtering through the Search Bar
• Log Analyzer
You can view Reports either as Summary reports for all or selected units on the Dell SonicWALL Analyzer network, or view detailed reports for individual units.
Viewing Available Firewall Report Types
To view the available types of reports for the Firewall appliances, perform the following steps:
1. Log into your Analyzer management console.
2. Click the Firewall tab.
3. Select an appliance or global view from the TreeControl.
4. Expand the desired selection on the Reports list and click on it.
Note: All Reports show a one-day period unless another interval is specified in the Time Bar.
The following types of reports are available:
Global Level Reports:
• Data Usage
– Summary: connections, listed by appliance, for one day (default)
• Applications
– Summary: connections, listed by application, for one day (default)
• Web Activity
– Summary: hits, listed by appliance, for one day (default)
• Web Filter
– Summary: access attempts, listed by appliance, for one day (default)
• VPN Usage
– Summary: VPN connections, listed by appliance, for one day (default)
• Threats
– Summary: connection attempts, listed by appliance, for one day (default)
Note: Summary Reports are not drillable and no Detail view is available.
Unit Level Reports
Detail views are available for all Report items unless otherwise noted.
• Data Usage
– Timeline: connections for one day (default)
– Initiators: Top Initiators, listed by IP address, Initiator Host, User, and Responder, displayed as a pie chart
– Responders: Top Responders, listed by IP address, Responder Host, and Initiator, displayed as a pie chart
– Services: connections, listed by service protocol, displayed as a pie chart
– Details: provides a shortcut to the Detail view normally reached by drilling down. Detail sections include: Initiators, Services, Responders, Initiator Countries, and Responder Countries. Additional filtering/drilldown takes you to the Log Analyzer
• Applications
– Data Usage connections, listed by application and threat level
– Detected: events, listed by application and threat level
– Blocked: blocked events, listed by application and threat level
– Categories: types of applications attempting access
– Initiators: events displayed by Initiator IP and Initiator host
– Timeline: events over one day
• User Activity
– Details: a detailed report of activity for the specified user
• Web Activity
– Category: hits and browse time listed by information category
– Sites: sites visited by IP, name, and category, with hits and browse time
– Initiators: Initiator host and IP with category and user
– Timeline: site hits with time of access and browse time
– Details: provides a shortcut to an access timeline and Detail view normally reached by drilling down. Detail sections include: Categories, Sites, and Initiators.
• Web Filter
– Category: hits and browse time listed by information category
– Sites: sites visited by IP, name, and category, with hits and browse time
– Initiators: Initiator host and IP with category and user
– Timeline: site hits with time of access and browse time
– Details: provides a shortcut to an access timeline and Detail view normally reached by drilling down. Detail sections include: Categories, Sites, and Initiators.
• VPN Usage
– Policies: lists connections by VPN Policy
– Initiators: Initiator host and IP with category and user
– Services: Top VPN Services by Service Protocol
– Timeline: VPN connections over a 1 day period
• Intrusions
– Detected: number of intrusion events by category
– Blocked: blocked intrusions and number of attempts at access
– Targets: number of intrusion events by target host and IP
– Initiators: Initiator host and IP with category and use
– Timeline: intrusions listed by time of day
– Details: provides a shortcut to an access timeline and Detail view normally reached by drilling down. Detail sections include: Categories, Sites, and Initiators.
– Alerts: provides a list of intrusion alerts
• Gateway Viruses
– Blocked: blocked virus attacks and number of attempts at access
– Targets: targeted hosts and IP addresses
– Initiators: initiating users, hosts, and IP addresses of the virus attack
– Timeline: times when the virus attempted to gain access, displayed over time
• Spyware
– Detected: spyware detected by the firewall
– Blocked: spyware blocked by the firewall
– Targets: targeted hosts and IP addresses
– Initiators: initiating users, hosts, and IP addresses of spyware download
– Timeline: times when the spyware accessed the system, displayed over time
• Attacks
– Attempts: type of attack and times access was attempted
– Targets: host and IP address, and number of times access was attempted
– Initiators: top attack initiators by IP and host
– Timeline: time and number of attempts at access, displayed over time
• Authentication: authenticated users, their IP addresses, and type of login/logout
– User Login
– Admin Login
– Failed Login
• Custom Reports: allows access to saved custom reports
• Analyzers
– Log Analyzer: provides a detailed event-by event listing of all activity. The Log Analyzer is drillable, but no Detail sections are available.
The Report contains a filter bar at the top, plus the actual Data Container. The default Data Container contains an interactive chart view, which contains either a grid view, containing a text version of the information. One or more sections may be present in the grid view. Toggle buttons allow you to display the Chart view, Grid view, or Chart and Grid view.
Grid sections are arranged in columns. Columns may be rearranged to view them from the top down or bottom up, by clicking the up and down arrows in the column headings. You can narrow results by applying a filter to a column: right-click on a column heading and click Add Filter.
Hypertext-linked columns are drillable, meaning you can click on the hypertext entry to bring up a Detail view with more information on the desired entry. Detail views might have multiple sections.
The Detail views are usually reflected in the sub-headings under the Reports list, which provide a shortcut directly to the Detail Report. To go to the full Detail view, click the Details entry in the Reports list. From the Detail view, you can access the system logs, for event-by-event information, or further filter the results. For more information on using the Log Analyzer to view and filter syslog reports, see Using the Log Analyzer.
Details views can contain multiple sections. To determine if you have reached the end of the list of sections, check for the time zone message, which indicates the end of the Detail View.
Reports with hyperlinked columns can be filtered on the column or by drilling down on the hyperlinked entry.
You can also get to a filtered Detail view by clicking the section representing the desired information in the pie chart.
To save a filtered view for later viewing, click on the Save icon on the Filter Bar. The saved view will now appear under Custom Reports.
To learn more about Custom reports, see Custom Reports
The sections contain the following information:
• Node information—Information on the firewall(s) is displayed at the global or unit level.
• Syslog Categories—The types of syslog data selected to be collected for the selected appliance.
• Syslog Servers—The IP address and Port number of the syslog servers configured to collect data from the selected appliance.
– Synchronize Appliance Information with Analyzer—Click the Synchronize Appliance Information Now link to refresh status data about the monitored appliances. This status information is normally updated every 24 hours.
• Getting Started With Analyzer—Click the Open Getting Started Instructions In New Window link to open the Analyzer installation and initial configuration instructions in a separate window.
The Firewall Summary reports display an overview of bandwidth, uptime, intrusions and attacks, and SRA usage for managed SonicWALL Firewall appliances. The security summary report provides data about worldwide security threats that can affect your network. The summaries also display data about threats blocked by the SonicWALL security appliance.
Viewing Global Summary Reports
Summary reports for data usage, applications, web usage and filtering, VPN usage, and threats for managed SonicWALL appliances are available at the global level, through the TreeControl menu. Summary reports are available for:
• Data Usage
• App Control
• Web Usage
• Web Filtering
• VPN Usage
• Threats
Group-level Summary reports provide an overview of information for all Firewalls under the group node for the specified period. The report covers the connections and transfers by appliance for Data Usage, App Control, and VPN Usage, For Web Usage and Web Filters, hits are also included. Web filters and Threats list attempts at connection. Unless specified differently in the Date Selector, the Summary report covers a single day. Global Summary reports are not drillable.
The Dashboard Summary report displays statistics, alerts, graphical summary reports, and a list of available custom report templates. Displayed statistics can include total bandwidth, total attacks and other measurable information. The alerts list is displayed when the configured threshold has been reached. A wide range of graphical reports are also available for display.
You can configure the Dashboard > Summary report contents in the Firewall > Configuration > Settings page.
To view the Summary report, perform the following steps:
1. Click the Firewall tab.
2. Select the global icon.
3. Click Data Usage > Summary.
The timelines at the top of the page display the totals, and the grid section sorts the information by appliance or applications.
Unit level reports display status for an individual SonicWALL appliance.
1. Click the Firewall tab.
2. Select the global icon or a SonicWALL appliance.
3. Click Data Usage > Timeline. (This is the default view when the Firewall Report interface comes up.)
Viewing User Activity Logs
Web User Activity logs allow you to filter results to view only the activity of a specific user.
The User Activity Analyzer provides a detailed report listing activity filtered by user. If a user report has been saved previously, bringing up the User Activity Analyzer will display a list of saved reports under the Filter Bar.
If you wish to create a new report, use the Filter Bar to create a new report.
1. Click the Firewall tab.
2. Select a SonicWALL appliance.
3. Click on User Activity > Details to bring up the User Activity Analyzer. The User Activity Analyzer generates a Detail report based on the user name.
If no user activity reports were saved, only the Filter Bar will display, with the User filter pre-selected. You can enter a specific user name, or use the LIKE operator wildcards (*) to match multiple names.
4. Enter the name of the user into the field and click the Go (arrow) button to generate the report
The customized User Activity Details report will display a timeline of events, Initiators, Responders, Services, Applications, Sites visited, Blocked site access attempted, VPN access policy in use, user authentication, Intrusions, Initiator Countries, and Responder Countries associated with that particular user.
Data for a particular user may not be available for all of these categories.
Viewing Applications Reports
Application Reports provide details on the applications detected and blocked by the firewall, and their associated threat levels.
1. Click the Firewall tab.
2. Select a SonicWALL appliance.
3. Click Application > Data Usage.
The Applications Report displays a pie chart with the application and threat level it poses.
You can drill down for additional Details views on connections over time (Timeline view), Data Usage, Detected applications, Blocked applications, Categories of applications, top initiators.
Viewing Web Activity Reports
Web Activity Reports provide detailed reports on browsing history.
1. Click the Firewall tab.
2. Select a SonicWALL appliance.
3. Click Web Activity > Categories.
The Web Activity Report displays a pie chart with the Top Categories of type of access, total browse time, and hits.
You can drill down for additional Details views on connections over time (Timeline view), Sites visited, Categories of sites, and Top Initiators. A Details entry links directly to the details view of all entries.
Viewing Web Filter Reports
Web Filter Reports provide detailed reports on attempts to access blocked sites and content.
1. Click the Firewall tab.
2. Select the global icon or a SonicWALL appliance.
3. Click Web Filter > Categories.
The Web Filter Report displays a pie chart with the Top Categories of blocked access and total attempts to access.
You can drill down for additional Details views on connections over time (Timeline view), Sites visited, Categories of sites, and Top initiators. A Details entry links directly to the details view of all entries.
Viewing VPN Usage Reports
VPN usage reports provide details on the services and policies used by users of virtual private networks.
1. Click the Firewall tab.
2. Select a SonicWALL appliance.
3. Click VPN Usage > Policies.
The VPN Usage Report displays total connections for each VPN Policy item as a pie chart and tabular grid view.
You can drill down for additional Details views on Service protocols and Top initiators.
Viewing Intrusions Reports
Intrusion Reports provide details on types of intrusions and blocked access attempts.
1. Click the Firewall tab.
2. Select a SonicWALL appliance.
3. Click Intrusions > Detected .
The Attacks report provides a pie chart and a list of the initiating IP addresses, hosts, and users, with number of attempts for each.
Drill down for additional Detail views of Intrusion Categories, Targets, Initiators, Ports affected, Target Countries, and Initiator Countries.
Viewing Gateway Viruses Reports
The Gateway Viruses reports provide details on the Top Viruses that were blocked when attempting to access the firewall.
1. Click the Firewall tab.
2. Select a SonicWALL appliance.
3. Click Gateway Viruses > Blocked .
The Top Viruses report appears.
The report provides details on the viruses blocked, the targets, initiators, and a timeline of when they attempted access.
Drilling down provides a list of virus identity, Targets, Initiators, Target Countries, and Initiator Countries.
Viewing Spyware Reports
The Spyware report gives details of the spyware that was detected and/or blocked, the targets, initiators, and a timeline of when they attempted access.
1. Click the Firewall tab.
2. Select a SonicWALL appliance.
3. Click Spyware > Detected.
The report provides details on the types of spyware detected and blocked, targets.
Drilling down provides a list of virus identity, Targets, Initiators, Target Countries, and Initiator Countries.Drilling down lists countries of origin, and target countries.
Viewing Attacks Report
The Attacks report lists attempts to gain access, target systems, initiators, and a timeline of when the attack occurred.
1. Click the Firewall tab.
2. Select a SonicWALL appliance.
3. Click Attacks > Attempts.
The Attacks report provides a pie chart and a list of the initiating IP addresses and hosts.
Drill down for additional Detail views of Intrusion Categories, Targets, Initiators, Ports affected, Target Countries, and Initiator Countries.
Viewing Authentication Reports
Authentication reports provide information on users attempting to access the Firewall.
1. Click the Firewall tab.
2. Select a SonicWALL appliance.
3. Click Authentication > User Login.
The Authentication report displays a list of authenticated users, their IP addresses, service, time they were logged in, and type of login/logout. Additional Reports are available for Administrator logins and failed login attempts.
Clicking on hyperlinks provides additional filtering for the reports.
You can filter on the Service to view SRA and other appliances by drilling down to the syslog.
1. Go to the filter bar and click on the + and select Service from the pull-down menu. Click on the = operator, and click on the field next to it to bring up the pull-down menu. Select SSLVPN from the pull-down
list
2. Click Go to view a report for that Service.
Note For the Duration and Service categories to be present, the Firewall appliance firmware must be at least version 5.6.0.
The Log Analyzer allows advanced users to examine raw data for status and troubleshooting. The Analyzer logs contain detailed information from the system logs on each transaction that occurred on the specified SonicWALL appliance. These logs can be filtered or drilled down to further narrow the focus of the information, allowing analysis of data about alerts, interfaces, bandwidth consumption, etc. The Log Analyzer is only available at the individual unit level.
Because of space constraints, some column items, particularly the log event messages, may not be fully visible in the Reports pane. To view the full report, export the report to an Excel spreadsheet to view, sort, or organize messages.
Log information can be saved for later analysis and reloaded from Custom Reports.
To load a report for viewing, either:
• Click Load Custom Report and select from the pull-down list of saved Custom Reports.
• Click on Analyzers > Log Analyzer to view the current log.
Note The Log Analyzer entries display raw log information for every connection. Depending on the amount of traffic, this can quickly consume a large amount of space in the database. It is highly recommended to be careful when choosing the number of days of information to be stored.
Viewing the Log Analyzer
The log displays information specific to either a particular report or overall system information, depending on the path used to reach the log, either from the individual report level or from the Log Analyzer entry on the Reports tab. Entries in the Analyzer log will vary, according to the relevant report type. You can customize the log entries by using the following options:
Show/Hide Log Columns
Use the Show/Hide Columns function to hide columns that you do not want to display in the Analyzer Log. Just click the Configure the Log Analyzer icon, then select the columns that you want to display and deselect the ones that you do not want to display. By configuring the displayed columns, the Log Analyzer gives a more clean, concise, and meaningful way to view the logs, instead of displaying unnecessary columns that take up valuable real estate.
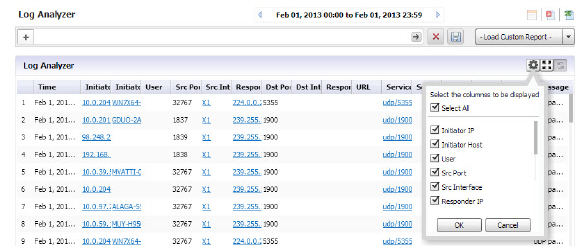
Note “Serial number” column and “Time” column are not part of the list to be configured because they are necessary for any displays.
Row-Based Expansion
Instead of showing all the column info at once, the row-based expansion simplifies the screen and gives on-demand info through a single click.
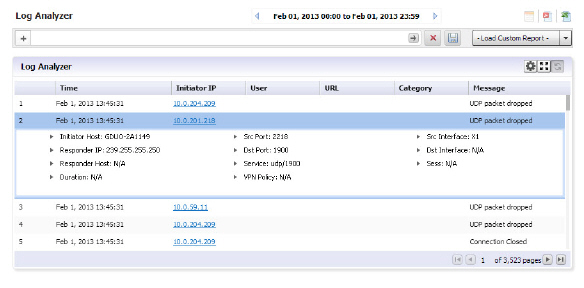
Click on each row to pull down the hidden column information.
Note This feature is only available after you sort the columns using the show/hide function.
Full Screen Mode
Switch to full screen mode by clicking the Full Screen Mode toggle icon. This will populate the entire browser screen with the Log Analyzer page, hiding the tree control and reports panels.

Session-Based Configurations
All column configurations for the Log Analyzer are recorded in each session. This is so that within the session, users can have the desired/configured tabular view of the Log Analyzer at all times.
Priority
The log event messages are color-keyed according to priority. Red is the highest priority, followed by yellow for Alerts. Messages without color keys are informational, only. The color categories are:
• Alert: Yellow
• Critical: Red
• Debug: White
• Emergency: Red
• Error: White
• Info: White
• Notice: White
• Warning: White
Color keys allow you to immediately focus on the priority level of the message, and filter data accordingly.
The Log Analyzer allows you to add filters to view user-or incident-specific data. The Log analyzer can be reached either by drilling down in individual reports, or from the Analyzers item under the Reports tab.
To view the Analyzer Log, perform the following steps:
1. Select a SonicWALL appliance from the TreeControl pane.
2. Click to expand the Analyzer tree and click on Log Analyzer. The saved Log Analyzer report page displays.
Note Because system logs have a large number of entries, it is advisable to constrain the number of entries displayed on the page.
Saved system logs are limited in the number of rows that will be saved. If saving to PDF, a maximum of 2500 rows will be saved. If saving to Excel, a maximum of 10,000 rows will be saved.
3. To add a filter, click on the + in the Filter Bar and specify the desired filter item and parameters.
Available filters include filters for Application, Category, DST Interface, DST Port, Duration, Initiator Country, Host, or IP address, Interface, Message, Priority, Responder country, IP, or Name, Service, Session, Src Interface, Src Port, URL, User, or VPN Policy. This full list is available from the Log Analyzer Entry.
If you are viewing the log in the Log Analyzer view for a specific application entry, only those filters specific to that entry will be available.
Log views are drillable, and will add filters as column entries are drilled. Click on an entry of interest to add a filter and further constrain the information displayed.
Log Analyzer Use Case
In the following use case, we will sort and filter the captured event information to evaluate threats targeted toward the X0 default interface.
On the Reports tab, click on Analyzers > Log Analyzers.
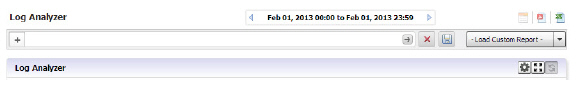
1. In the Log Analyzer, click on the + to add a filter, and select the Interface filter.
2. Type in X1 to specify the default interface filter.
3. Click on the Go button.
The Log Analyzer will be filtered on the X1 port interface.
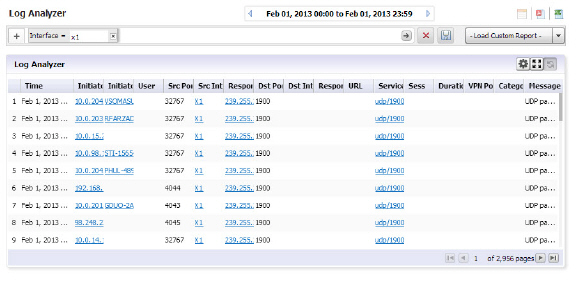
This will allow you to begin debugging, or further investigate use of the database.
More information can also be found by using Universal Scheduled Reports.
Configuration settings allow you to set up certain parameters for how data is displayed in Reports. You can set up currency cost per Megabyte for the Summarizer, or add filters for the Log Analyzer reports.
Setting Up Currency Cost for Summarizer
The Data Usage page contains a Cost per connection entry. You can set what currency and the cost per Megabyte.
1. Click Configuration > Settings on the Reports tab.
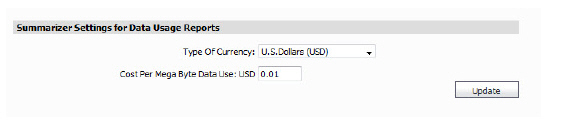
2. Select the currency of the desired country and the cost per MB.
3. Click Update. The cost will be immediately reflect on the Data Usage page.
Adding Syslog Exclusion Filters
Exclusion Filters restrict what information is used to generate Reports. This is achieved by filtering out syslogs (based on the criteria specified in the Syslog Filter screen) from being uploaded to the Reports database. These filtered syslogs are, however, stored in the file system and archived, thus ensuring that all syslogs are available for audit trailing purposes. Excluding data from being uploaded to the Reporting database in this way can be useful in maintaining confidentiality regarding use history, or eliminating data corresponding to certain users who are not of interest. For instance, you might use an Exclusion Filter to eliminate data from the company CEO. This screen is used to specify syslog filters for the unit selected in the TreeControl. A similar screen exists for system wide syslog filtering, in the Console Panel’s Reports > Syslog Filter screen
1. To add an Exclusion filter, click on Configuration > Filters.
The Syslog Exclusion Filter page comes up. This page allows you to view what filters are currently applied, add filters, or remove filters.
2. To configure and add an Exclusion Filter, click Add Filter. The Add Filter menu comes up.
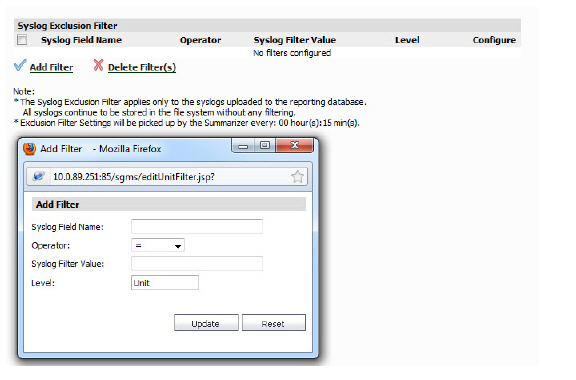
3. Specify the field you want to modify, and select an operator and value. Click Update.
The Reports will now be filtered according to the selected criteria. Exclusion Filter settings are picked up by the Summarizer at specified regular intervals.
You can configure a report with customized filters, then save it for later viewing and analysis. Saving a Report allows you to view it later, by loading it through the Custom Reports interface. Custom Reports can either be saved directly, or configured through Universal Scheduled Reports. You can either load the report through the Custom Report pull-down on the Search Bar, or click Reports > Custom and choose from the list of saved Custom reports.
Regularly scheduled Custom Reports can be configured through the Universal Scheduled Reports interface, accessible through the Custom Reports icon in the upper right corner. These reports can be set up to be emailed to you on a regular schedule.
Custom Reports are available at the unit level for all appliances visible on the Firewall tab. The Log Analyzer must be enabled for the appliance.
The Manage Reports screen (Custom Reports > Manage Reports) allows you to view what Custom Reports are available and delete reports from the system.
For more information on configuring and scheduling custom Reports refer to the Universal Scheduled Reports section.