Deployment_Guidelines
This sections provides information about deployment guidelines for the SRA appliance. This section contains the following subsections:
• Support for Numbers of User Connections
• Integration with Dell SonicWALL Products
Support for Numbers of User Connections
The following table lists the maximum and recommended numbers of concurrent tunnels supported for each appliance.
|
Factors such as the complexity of applications in use and the sharing of large files can impact performance.
The following table describes the types of applications or resources you can access for each method of connecting to the SRA appliance.
|
Integration with Dell SonicWALL Products
The SRA appliance integrates with other Dell SonicWALL products, complementing the Dell SonicWALL NSA, PRO and TZ Series product lines. Incoming HTTPS traffic is redirected by a Dell SonicWALL firewall appliance to the SRA appliance. The SRA appliance then decrypts and passes the traffic back to the firewall where it can be inspected on its way to internal network resources.
The SRA appliance is commonly deployed in tandem in one-armed mode over the DMZ or Opt interface on an accompanying gateway appliance, for example, a Dell SonicWALL network security appliance, such as a NSA 4500.
This method of deployment offers additional layers of security control plus the ability to use Dell SonicWALL’s Unified Threat Management (UTM) services, including Gateway Anti-Virus, Anti-Spyware, Content Filtering and Intrusion Prevention, to scan all incoming and outgoing NetExtender traffic. Dell SonicWALL recommends one-armed mode deployments over two-armed for the ease-of-deployment and for use in conjunction with UTM GAV/IPS for clean VPN.
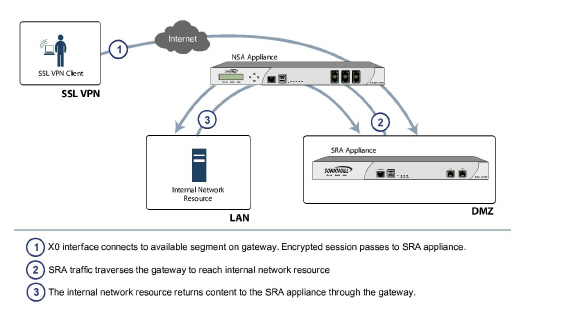
As shown below, in one-armed mode the primary interface (X0) on the SRA appliance connects to an available segment on the gateway device. The encrypted user session is passed through the gateway to the SRA appliance (step 1). The SRA appliance decrypts the session and determines the requested resource. The SRA session traffic then traverses the gateway appliance (step 2) to reach the internal network resources. While traversing the gateway, security services, such as Intrusion Prevention, Gateway Anti-Virus and Anti-Spyware inspection can be applied by appropriately equipped gateway appliances. The internal network resource then returns the requested content to the SRA appliance through the gateway (step 3) where it is encrypted and returned to the client.
Figure 2:7 Sequence of Events in Initial Connection
For information about configuring the SRA appliance to work with third-party gateways, refer to Configuring the SRA Appliance with a Third-Party Gateway.
The SRA appliances also support two-armed deployment scenarios, using one external (DMZ or WAN side) interface and one internal (LAN) interface. However, two-armed mode introduces routing issues that need to be considered before deployment. The SRA appliance does not route packets across interfaces, as there are IP tables rules preventing that, and therefore cannot be used as a router or default gateway. Any other machines connected to an internal interface of the SRA appliance in two-armed mode would need to access the Internet or other network resources (DNS, NTP) through a different gateway.
If you have an internal router as well as an Internet router, you can use a two-armed deployment to leverage your internal router to access your internal resources.
Sample Scenario - Company A has resources and a number of subnets on their internal network, and they already have a robust routing system in place. With two-armed deployment of the SRA appliance, client requests destined for internal resources on the corporate network can be delivered to an internal router.