|
1
|
Click the Reports tab.
|
Click Data Usage > Timeline. (This is the default view when the Firewall Report interface comes up.)
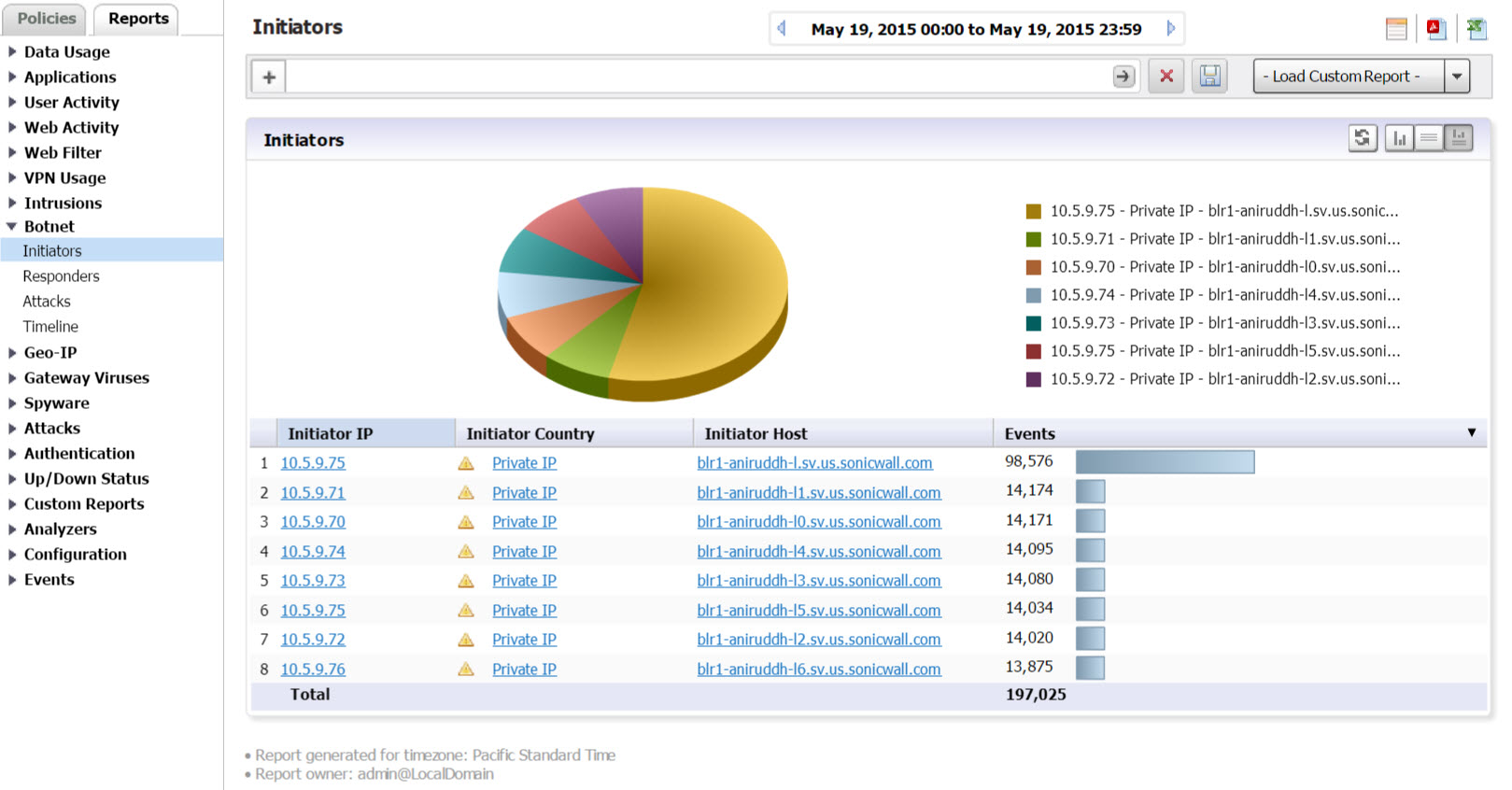
This report is drillable. Click on an Initiator IP entry to break the Timeline report down into its Detail View report groups for the selected IP address. These groups also contain drillable hyperlinks that takes you to more specific Detail View information. The columns can also be filtered. For more information on drilling down in a report, refer to Drilling Down
|
•
|
|
•
|
|
1
|
Click the Reports tab.
|
|
3
|
Click on User Activity > Details to bring up the User Activity Analyzer. The User Activity Analyzer generates a Detail report based on the user name.
|
|
4
|
Enter the name of the user into the field and click Go (arrow) to generate the report.
|
|
1
|
Click the Reports tab.
|
|
3
|
Click Applications > Data Usage.
|
|
1
|
Click the Reports tab.
|
|
3
|
Click Web Activity > Categories.
|
|
1
|
Click the Reports tab.
|
|
3
|
Click Web Filter > Categories.
|
|
1
|
Click the Reports tab.
|
|
3
|
Click VPN Usage > Policies.
|
|
1
|
Click the Reports tab.
|
|
3
|
Click Intrusions > Detected.
|
|
1
|
Click the Reports tab.
|
|
3
|
Click Botnet > Initiators.
|
|
1
|
Click the Reports tab.
|
|
3
|
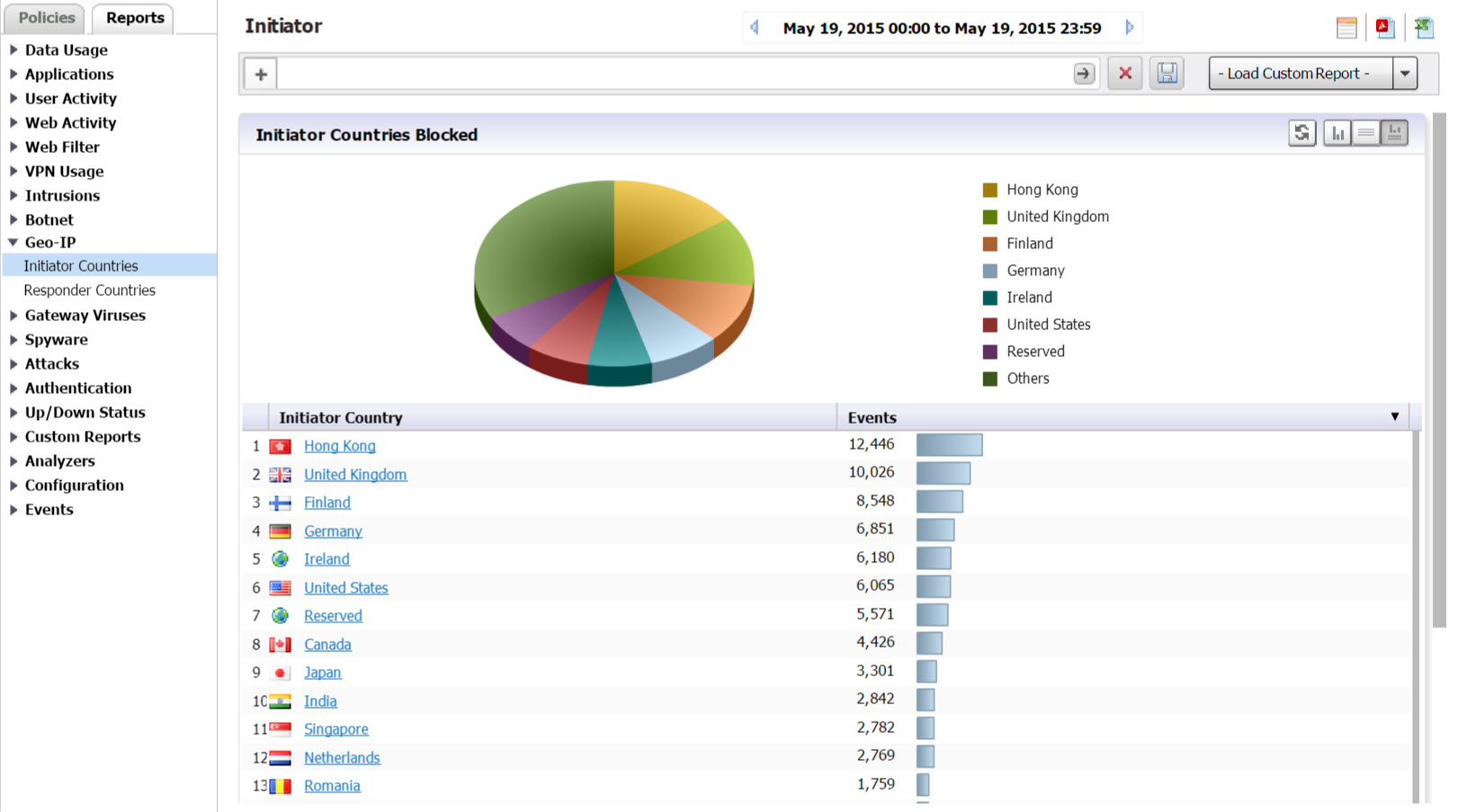
Click Geo-IP > Initiator Countries.
|
Drill down for additional detailed views of Initiator IPs, Hosts, Initiator MACs, Users, and Events.
|
1
|
Click the Reports tab.
|
|
3
|
Click Gateway Viruses > Blocked.
|
|
1
|
Click the Reports tab.
|
|
3
|
Click Spyware > Detected.
|
|
1
|
Click the Reports tab.
|
|
3
|
Click Attacks > Attempts.
|
|
1
|
Click the Reports tab.
|
|
3
|
Click Authentication > User Login.
|
|
1
|
Go to the filter bar and click on the + and select Service from the pull-down menu. Click the = operator, and click on the field next to it to bring up the pull-down menu. Select SSLVPN from the pull-down list
|
|
2
|
Click Go to view a report for that Service.
|
|
Select Default for a default range of colors.
Select Generate to generate a random range of colors.
If a gradient is desired, select the Use Gradient box located below the text fields.
|
||
|
The Pause button appears gray if the data flow has been frozen.
|
||
The Multi-Core Monitor displays dynamically updated statistics on utilization of the individual cores of the SonicWALL SuperMassive. Core 1 through core 8 handles the control plane. Core 1 through core 8 usage is displayed in green on the Multi-Core Monitor. The remaining cores handle the data plane. To maximize processor flexibility, functions are not dedicated to specific cores; instead all cores can process all data plane tasks. Memory is shared across all cores. Each core can process a separate flow simultaneously, allowing for up to 88 flows to be processed in parallel.
The Flow Analytics Filter Options allows the administrator to filter out incoming, real-time data. Administrators can apply, create, and delete custom filters to customize the information they wish to view. The Filter Options apply across all the Application Flow tabs. Refer to Using Filtering Options .
|
•
|
The URLs tab displays a list of URLs currently accessed by Users.
|
The Group option sorts data based on the specified group. Each tab contains different grouping options.
|
•
|
Check Box: Allows the administrator to select the line item for creation of filters.
|
|
•
|
Main Column: The title of the Main Column is dependent on the selected tab. For example, if the Users Tab is the selected, then the Main Column header reads “Users.” In that column, the name of the Users connected to the network are shown. Clicking on the items in this column brings up a popup with relevant information on the item displayed.
|
|
•
|
Sessions: Clicking on this number brings up a table of all active sessions.
|
|
•
|
Packets: Displays the number of data packets transferred.
|
|
•
|
Bytes: Displays the number of bytes transferred.
|
|
•
|
Rate (KBps): Displays the rate at which data is transferred.
|
|
•
|
Threats: Displays the number of threats encountered by the network.
|
|
•
|
Total: Displays the total Sessions, Packets, and Bytes sent during the duration of the current interval.
|
|
1
|
Navigate to Flow Activity > Flow Analytics > Applications. Select the check boxes of the applications you wish to add to the filter. In this case, Ventrilo is selected.
|
|
2
|
Click Filter View to add Ventrilo to the filter.
|
|
•
|
The Applications tab displays a list of Applications currently accessing the network.
|
|
•
|
The Users tab displays a list of Users currently connected to the network.
|
|
•
|
The IP tab displays a list of the IP addresses currently accessing the network.
|
|
•
|
The Viruses tab displays a list of detected viruses on the network.
|
|
•
|
The Intrusions tab displays a list of the attempted intrusions over the selected time period.
|
|
•
|
The Spyware tab displays a list of detected spyware on the network.
|
|
•
|
The Location tab displays a list of locations that users are accessing the network from.
|
|
•
|
The URL Rating tab displays a list of rated URLs on the network.
|