For an introduction to RADIUS authentication in SonicOS, see Using RADIUS for Authentication . If you selected RADIUS or RADIUS + Local Users from the Authentication method for login drop-down menu on the Users > Settings page, the Configure RADIUS button becomes available.
A separate Configure button for RADIUS is also available if you selected Browser NTLM authentication only from the Single-sign-on method choices. The configuration process is the same.
|
1
|
Navigate to the Users > Settings page.
|
|
2
|
Click Configure RADIUS to set up your RADIUS server settings in SonicOS. The RADIUS Configuration dialog displays.
|
|
3
|
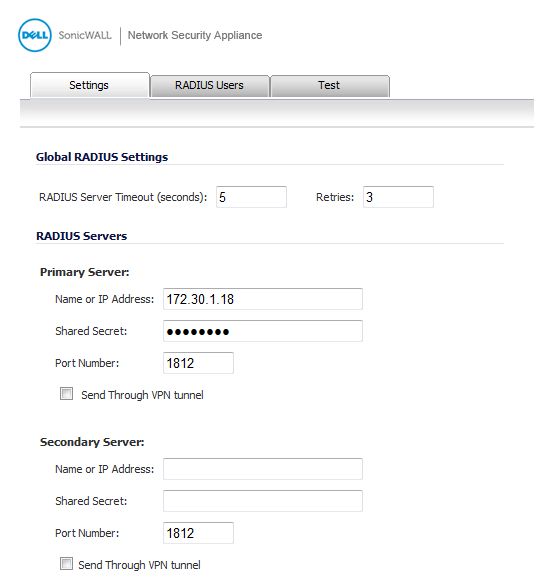
Under Global RADIUS Settings, type in a value for the RADIUS Server Timeout (seconds). The allowable range is 1-60 seconds with a default value of 5.
|
|
4
|
In the Retries field, enter the number of times SonicOS will attempt to contact the RADIUS server. If the RADIUS server does not respond within the specified number of retries, the connection is dropped. This field can range between 0 and 10, with a default setting of 3 RADIUS server retries.
|
|
5
|
In the RADIUS Servers section, designate the primary RADIUS server. In the Primary Server section, type the host name or IP address of the RADIUS server in the Name or IP Address field.
|
|
6
|
Type the RADIUS server administrative password or “shared secret” in the Shared Secret field. The alphanumeric Shared Secret can range from 1 to 31 characters in length. The shared secret is case sensitive.
|
|
7
|
Type the Port Number for the RADIUS server to use for communication with SonicOS. The default is 1812.
|
|
8
|
Optionally, select Send Through VPN tunnel.
|
|
9
|
In the Secondary Server section, optionally type the host name or IP address of the secondary RADIUS server in the Name or IP Address field.
|
|
10
|
|
11
|
|
•
|
OK if you have finished configuring the RADIUS server.
|
|
•
|
Apply, to continue configuring RADIUS users (see RADIUS Users Tab ) and/or testing the settings (see RADIUS Client Test ).
|
On the RADIUS Users tab you can specify what types of local or LDAP information to use in combination with RADIUS authentication. You can also define the default user group for RADIUS users.
|
1
|
Click the RADIUS Users tab.
|
|
2
|
Select Allow only users listed locally if only the users listed in the SonicOS database are authenticated using RADIUS.
|
|
3
|
Select the Mechanism used for setting user group memberships for RADIUS users option:
|
|
NOTE: If the Use SonicWALL vendor-specific attribute on Radius server or Use RADIUS Filter-ID attribute on RADIUS server options are selected, the RADIUS server must be properly configured to return these attributes to the Dell SonicWALL appliance when a user is authenticated. The RADIUS server should return aero (0) or more instances of the selected attribute, each giving the name of a user group to which the user belongs.
For details of the vendor-specific attribute settings, see the tech note, SonicOS Enhanced: Using User Level Authentication, and the SonicOS Enhanced RADIUS Dictionary file, SonicWALL.dct. Both are available at https://support.software.dell.com/. |
|
•
|
Use SonicWALL vendor-specific attribute on RADIUS server – To apply a configured vendor-specific attribute from the RADIUS server. The attribute must provide the user group to which the user belongs. The preferred vendor-specific RADIUS attribute is SonicWall-User-Group. SonicWall-User-Privilege also works for certain user groups, but it is supported primarily for backwards compatibility and is not governed by the Mechanism for setting user group memberships for RADIUS users setting; that is, it is still effective even if something other than the Use SonicWALL vendor-specific attribute on RADIUS server is selected.
|
|
•
|
Use RADIUS Filter-ID attribute on RADIUS server – To apply a configured Filter-ID attribute from the RADIUS server. The attribute must provide the user group to which the user belongs.
|
|
•
|
Use LDAP to retrieve user group information (default) – To obtain the user group from the LDAP server. You can click the Configure button to set up LDAP if you have not already configured it or if you need to make a change. For information about configuring LDAP, see Configuring the Dell SonicWALL Appliance for LDAP .
|
|
•
|
Local configuration only – If you do not plan to retrieve user group information from RADIUS or LDAP.
|
|
•
|
Memberships can be set locally by duplicating RADIUS user names – For a shortcut for managing RADIUS user groups. When you create users with the same name locally on the security appliance and manage their group memberships, the memberships in the RADIUS database automatically change to mirror your local changes.
|
|
4
|
If you have previously configured User Groups in SonicOS, select the group from the Default user group to which all RADIUS users belong drop-down menu. To create a new user group, see Creating a New User Group for RADIUS Users .
|
|
•
|
OK if you have finished configuring the RADIUS server.
|
|
•
|
Apply, to continue configuring RADIUS users and/or testing the settings.
|
In the RADIUS User Settings dialog, you can create a new group by choosing Create a new user group... from the Default user group to which all RADIUS users belong drop-down menu. The Add Group dialog displays. For the procedure for creating a new user group, see Creating or Editing a Local Group .
When RADIUS is used for user authentication, there is an option on the RADIUS Users tab in the RADIUS Configuration dialog to allow LDAP to be selected as the mechanism for setting user group memberships for RADIUS users:
When Use LDAP to retrieve user group information is selected, after authenticating a user via RADIUS, his/her user group membership information will be looked up via LDAP in the directory on the LDAP/AD server.
|
NOTE: If this mechanism is not selected, and one-time password is enabled, a RADIUS user will be receive a one-time password fail message when attempting to login through SSL VPN.
|
Clicking the Configure button launches the LDAP Configuration dialog. For more information on configuring LDAP settings, see Preparing Your LDAP Server for Integration .
In the RADIUS Configuration dialog, you can test your RADIUS Client user name, password and other settings by typing in a valid user name and password and selecting one of the authentication choices for Test. Performing the test applies any changes you have made.
|
1
|
Click the Test tab.
|
|
2
|
In the User field, type a valid RADIUS login name.
|
|
3
|
In the Password field, type the password.
|
|
4
|
For Test, select one of the following:
|
|
•
|
Password authentication: Select this to use the password for authentication.
|
|
•
|
CHAP: Select this to use the Challenge Handshake Authentication Protocol. After initial verification, CHAP periodically verifies the identity of the client by using a three-way handshake.
|
|
•
|
MSCHAP: Select this to use the Microsoft implementation of CHAP. MSCHAP works for all Windows versions before Windows Vista.
|
|
•
|
MSCHAPv2: Select this to use the Microsoft version 2 implementation of CHAP. MSCHAPv2 works for Windows 2000 and later versions of Windows.
|
|
5
|
Click the Test button. If the validation is successful, the Status messages changes to Success. If the validation fails, the Status message changes to Failure.
|