This chapter describes how to configure and manage the Application Firewall feature in SonicWALL SonicOS Enhanced. This chapter contains the following sections:
This section provides an introduction to the SonicOS Enhanced Application Firewall feature. This section contains the following subsections:
Application Firewall is a set of application-specific policies that gives you granular control over network traffic on the level of users, email users, schedules, and IP-subnets. The primary functionality of this application-layer access control feature is to regulate Web browsing, file transfer, email, and email attachments.
Application Firewall’s digital rights management component provides the ability to scan files and documents for content and keywords. Using Application Firewall, you can restrict transfer of certain file names, file types, email attachments, attachment types, email with certain subjects, and email or attachments with certain keywords or byte patterns. You can deny internal or external network access based on various criteria.
Based on SonicWALL’s Deep Packet Inspection technology, Application Firewall also features intelligent prevention functionality which allows you to create custom, policy-based actions. Examples of custom actions include the following:
While Application Firewall primarily provides application level access control, application layer bandwidth management and digital rights management functionality, it also includes the ability to create pure custom IPS signatures. You can create a custom policy that matches any protocol you wish, by matching a unique piece of the protocol header. See “Custom Signature” .
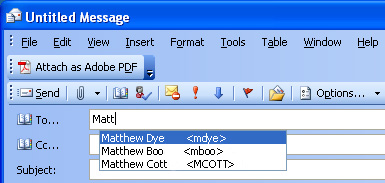
Application Firewall provides excellent functionality for preventing the accidental transfer of proprietary documents. For example, when using the automatic address completion feature of Outlook Exchange, it is a common occurrence for a popular name to complete to the wrong address. See the following figure for an example.
Application Firewall functionality can be compared to three main categories of products:
Standalone proxy appliances are typically designed to provide granular access control for a specific protocol. SonicWALL Application Firewall provides granular, application level access control across multiple protocols, including HTTP, FTP, SMTP, and POP3. Because Application Firewall runs on your SonicWALL firewall, you can use it to control both inbound and outbound traffic, unlike a dedicated proxy appliance that is typically deployed in only one direction. Application Firewall provides better performance and scalability than a dedicated proxy appliance because it is based on SonicWALL’s proprietary Deep Packet Inspection technology.
Today’s integrated application proxies do not provide granular, application level access control, application layer bandwidth management, and digital rights management functionality. As with dedicated proxy appliances, SonicWALL Application Firewall provides much higher performance and far greater scalability than integrated application proxy solutions.
While some standalone IPS appliances provide protocol decoding support, none of these products supports granular, application level access control, application layer bandwidth management, and digital rights management functionality.
In comparing Application Firewall to SonicWALL Email Security, there are benefits to using either. Email Security only works with SMTP, but it has a very rich policy space. Application Firewall works with SMTP, POP3, HTTP, FTP and other protocols, is integrated into SonicOS on the firewall, and has higher performance than Email Security. However, Application Firewall does not offer all the policy options for SMTP that are provided by Email Security.
Application Firewall scans application layer network traffic as it passes through the gateway and looks for content that matches configured keywords. When it finds a match, it performs the configured action. It can match text or binary content. When you configure Application Firewall, you create policies that define the type of applications to scan, the direction, the content or keywords to match, optionally the user or domain to match, and the action to perform.
The following sections describe the four main components of Application Firewall:
You can use Application Firewall to create custom policies to control specific aspects of traffic on your network. A policy is a set of application objects, properties, and specific prevention actions. When you create a policy using the Policy Setting window, you first create an application object, then select and optionally customize an action, then reference these when you create the policy.
Some examples of policies include:
|
•
|
Do not allow outgoing email or MS Word attachments with the keywords “SonicWALL
Confidential”, except from the CEO and CFO
|
|
•
|
When you create a policy, you select a policy type. Each policy type specifies the values or value types that are valid for the source, destination, application object type, and action fields in the policy. You can further define the policy to include or exclude specific users or groups, select a schedule, turn on logging, and specify the connection side as well as basic or advanced direction types. A basic direction type simply indicates inbound or outbound. An advanced direction type allows zone to zone direction configuration, such as from the LAN to the WAN.
The following table describes the characteristics of the available policy types.
|
Policy
Type
|
Valid
Source Service / Default
|
Valid
Destination Service / Default
|
Valid
Application Object Type
|
Valid Action
Type
|
Connection
Side
|
|
|
SMTP Client |
Policy which is applicable to SMTP traffic that originates on the client |
Any / Any (grayed out) |
SMTP / SMTP (grayed out) |
Filename, file extension, Email To (MIME), Email From (MIME), CC, Subject, Email body, Custom MIME header, File Content Object, E-Mail Size, Custom Object |
Reset/Drop, Disable attachment, Block SMTP E-Mail with Error Reply, Block SMTP E-Mail Without Reply, Email – Add Text, Bypass DPI, no action |
|
|
HTTP Client Request |
Policy which is applicable to Web browser traffic or any HTTP request that originates on the client |
Any / Any (grayed out) |
Any / HTTP (configurable) |
User-Agent, Host, URI content, Cookie, Web Browser, Referrer, filename, file extension HTTP request custom header, custom object |
Reset/Drop, Block page, HTTP redirect, Manage Bandwidth, Bypass DPI, no action |
|
|
HTTP Server Response |
Response originated by an HTTP Server |
Any / HTTP (configurable) |
Any / Any (grayed out) |
Set-Cookie header, Active-X ClassID, HTTP Response custom header, custom object |
Reset/Drop, Manage Bandwidth, Bypass DPI, no action |
|
|
FTP Client Request |
Any FTP command transferred over the FTP control channel |
Any / Any (grayed out) |
FTP Control / FTP Control (grayed out) |
FTP Command, FTP Command + Value, Custom Object |
FTP error notification, Reset/Drop, Bypass DPI, no action |
|
|
FTP Client File Upload Request |
An attempt to upload a file over FTP (STOR command) |
Any / Any (grayed out) |
FTP Control / FTP Control (grayed out) |
Filename, file extension |
FTP error notification, Manage Bandwidth, Reset/Drop, Bypass DPI, no action |
|
|
FTP Client File Download Request |
An attempt to download a file over FTP (RETR command) |
Any / Any (grayed out) |
FTP Control / FTP Control (grayed out) |
Filename, file extension |
FTP error notification, Manage Bandwidth, Reset/Drop, Bypass DPI, no action |
|
|
FTP Data Transfer Policy |
Data transferred over the FTP Data channel |
Any / Any (grayed out) |
Any / Any (grayed out) |
File Content Object |
Reset/Drop, Bypass DPI, no action |
|
|
POP3 Client Request |
POP3 Client request |
Any / Any (grayed out) |
POP3 / POP3 (grayed out) |
Custom Object |
Reset/Drop, no action |
|
|
POP3 Server Response |
Email downloaded from POP3 server |
POP3 / POP3 (grayed out) |
Any / Any (grayed out) |
Filename, file extension, Email To (MIME), Email From (MIME), CC, Subject, Email body, Custom MIME header, Custom Object |
Reset/Drop, Disable attachment, Bypass DPI, no action |
|
|
IPS-style custom signature |
Any / Any |
Custom Object |
Reset/Drop, Manage Bandwidth, Bypass DPI, no action |
Client side, Server Side, Both |
||
|
Dynamic Content |
IPS signature objects |
Signature Category List, Signature List |
Reset/Drop, Manage Bandwidth, Bypass DPI, no action |
Application objects represent the set of conditions which must be matched in order for actions to take place. This includes the object type, the match type (exact, partial, prefix, or suffix), the input representation (text or hexadecimal), and the actual content to match.
Hexadecimal input representation is used to match binary content such as executable files, while text input representation is used to match things like file or email content. You can also use hexadecimal input representation for binary content found in a graphic image. You could also use text input representation to match the same graphic if it contains a certain string in one of its properties fields.
The maximum size for an application object is 8192 (8K) bytes. Because Application Firewall matches data at wire speeds, application objects do not provide matching for regular expressions. You can use a proxy server for this functionality.
The File Content application object type provides a way to match a pattern within a compressed file. This type of application object can only be used with FTP Data Transfer or SMTP Client Policies.
The following table describes the supported application object types.
|
Negative
Matching
|
||||
|
Class ID of an Active-X component. For example, ClassID of Gator Active-X component is “c1fb8842-5281-45ce-a271-8fd5f117ba5f” |
||||
|
Allows specification of an IPS-style custom set of conditions. |
There are 4 additional, optional parameters that can be set: offset (describes from what byte in packet payload we should start matching the pattern – starts with 1; helps minimize false positives in matching), depth (describes at what byte in the packet payload we should stop matching the pattern – starts with 1), minimum payload size and maximum payload size. |
|||
|
Any content in the body of an email. |
||||
|
Email CC (MIME Header) |
Any content in the CC MIME Header. |
Exact, Partial, Prefix, Suffix |
||
|
Email From (MIME Header) |
Any content in the From MIME Header. |
Exact, Partial, Prefix, Suffix |
||
|
Allows specification of the maximum email size that can be sent. |
||||
|
Email Subject (MIME Header) |
Any content in the Subject MIME Header. |
Exact, Partial, Prefix, Suffix |
||
|
Email To (MIME Header) |
Any content in the To MIME Header. |
Exact, Partial, Prefix, Suffix |
||
|
MIME Custom Header |
Allows for creation of MIME custom headers. |
Exact, Partial, Prefix, Suffix |
A Custom header name needs to be specified. |
|
|
Allows specification of a pattern to match in the content of a file. The pattern will be matched even if the file is compressed. |
‘Disable attachment’ action should never be applied to this object. |
|||
|
In cases of email, this is an attachment name. In cases of HTTP, this is a filename of an uploaded attachment to the Web mail account. In cases of FTP, this is a filename of an uploaded or downloaded file. |
Exact, Partial, Prefix, Suffix |
|||
|
In cases of email, this is an attachment filename extension. In cases of HTTP, this is a filename extension of an uploaded attachment to the Web mail account. In cases of FTP, this is a filename extension of an uploaded or downloaded file. |
||||
|
Allows selection of specific FTP commands. |
||||
|
FTP Command + Value |
Allows selection of specific FTP commands and their values. |
Exact, Partial, Prefix, Suffix |
||
|
HTTP Cookie Header |
Allows specification of a Cookie sent by a browser. |
Exact, Partial, Prefix, Suffix |
||
|
Content found inside of the HTTP Host header. Represents hostname of the destination server in the HTTP request, such as www.google.com . |
Exact, Partial, Prefix, Suffix |
|||
|
HTTP Referrer Header |
Allows specification of content of a Referrer header sent by a browser – this can be useful to control or keep statistics of which Web sites redirected a user to customer’s Web site. |
Exact, Partial, Prefix, Suffix |
||
|
HTTP Request Custom Header |
Allows creation of custom HTTP Request headers. |
Exact, Partial, Prefix, Suffix |
A Custom header name needs to be specified. |
|
|
HTTP Response Custom Header |
Allows creation of custom HTTP Response headers. |
Exact, Partial, Prefix, Suffix |
A Custom header name needs to be specified. |
|
|
HTTP Set Cookie Header |
Set-Cookie headers. Provides a way to disallow certain cookies to be set in a browser. |
Exact, Partial, Prefix, Suffix |
||
|
Any content found inside of the URI in the HTTP request |
Exact, Partial, Prefix, Suffix |
|||
|
HTTP User-Agent Header |
Any content inside of a User-Agent header. For example: User-Agent: Skype. |
Exact, Partial, Prefix, Suffix |
||
|
Allows selection of specific Web browsers (MSIE, Netscape, Firefox). |
||||
|
Signature Category List |
Allows selection of one or more IPS signature groups. Each group contains multiple pre-defined IPS signatures. |
|||
|
Allows selection of one or more specific IPS signatures for enhanced granularity. |
You can see the available types of application objects in a drop-down list in the Application Objects Setting screen.
In the Application Object screen, you can add multiple entries to create a list of content elements to match. All content that you provide in an application object is case-insensitive for matching purposes. A hexadecimal representation is used to match binary content. You can use a hex editor or a network protocol analyzer like Wireshark (formerly Ethereal) to obtain hex format for binary files. For more information about these tools, see the following sections:
You can use the Load From File button to import content from predefined text files that contain multiple entries for an application object to match. Each entry in the file must be on its own line. The Load From File feature allows you to easily move Application Firewall settings from one SonicWALL security appliance to another.
Multiple entries, either from a text file or entered manually, are displayed in the List area. List entries are matched using the logical OR, so if any item in the list is matched, the action for the policy is executed.
An application object can include a total of no more than 8000 characters. If each element within an application object contains approximately 30 characters, then you can enter about 260 elements. The maximum element size is 500 bytes.
Negative matching provides an alternate way to specify which content to block. You can enable negative matching in an application object when you want to block everything except a particular type of content. When you use the object in a policy, the policy will execute actions based on absence of the content specified in the application object. Multiple list entries in a negative matching application object are matched using the logical AND, meaning that the policy action is executed only when all specified negative matching entries are matched.
Although all Application Firewall policies are DENY policies, you can simulate an ALLOW policy by using negative matching. For instance, you can allow email .txt attachments and block attachments of all other file types. Or you can allow a few types, and block all others.
Not all application object types can utilize negative matching. For those that can, you will see the Enable Negative Matching checkbox on the Application Object Settings screen.
Actions define how the Application Firewall policy reacts to matching events. You can choose a customizable action or select one of four predefined, default actions.
The four predefined actions are:
The seven customizable actions are:
Note that only the seven customizable actions are available for editing in the Application Firewall Action Settings dialog box. The four predefined actions cannot be edited or deleted. When you create a policy, the Policy Settings dialog box provides a way for you to select from the predefined actions along with any customized actions that you have defined.
The following table describes the available action types.
|
Predefined
or Custom
|
||
|
Policies can be specified without any action. This allows “log only” policy types. |
||
|
For TCP, the connection will be reset. For UDP, the packet will be dropped. |
||
|
Block SMTP Email Without Reply |
Blocks SMTP email, but to the sender it looks like email was successfully sent. |
|
|
Bypasses Deep Packet Inspection components IPS, GAV, Anti-Spyware and Application Firewall. This action persists for the duration of the entire connection as soon as it is triggered. Special handling is applied to FTP control channels that are never bypassed for Application Firewall inspection. This action supports proper handling of the FTP data channel. |
||
|
Block SMTP Email - Send Error Reply |
Blocks SMTP email and notifies the sender with a customized error message. |
|
|
Disable Email Attachment - Add Text |
Disables attachment inside of an email and adds customized text. |
|
|
Sends text back to the client over the FTP control channel without terminating the connection. |
||
|
Allows a custom HTTP block page configuration with a choice of colors. |
||
|
Provides HTTP Redirect functionality. For example, if
someone would like to redirect people to the Google Web site, the customizable part will look like: |
||
|
Allows definition of bandwidth management constraints with same semantics as Access Rule BWM policy definition. |
Application layer bandwidth management allows you to create policies that regulate bandwidth consumption by specific file types within a protocol, while allowing other file types to use unlimited bandwidth. This enables you to distinguish between desirable and undesirable traffic within the same protocol. Application layer bandwidth management is supported for HTTP Client, HTTP Server, Custom, and FTP file transfer policies. For details about policy types, see “Policies” .
For example, as an administrator you might want to limit .mp3 and executable file downloads during work hours to no more than 1 Mbps. At the same time, you want to allow downloads of productive file types such as .doc or .pdf up to the maximum available bandwidth, or even give the highest possible priority to downloads of the productive content. As another example, you might want to limit bandwidth for a certain type of peer-to-peer (P2P) traffic, but allow other types of P2P to use unlimited bandwidth. Application layer bandwidth management allows you to create policies to do this.
Application layer bandwidth management functionality is supported with a Bandwidth Management type action, available when adding a new action from the Application Firewall > Actions screen.
Application layer bandwidth management configuration is handled in the same way as the current bandwidth management configuration associated with Firewall > Access Rules. However, with Application Firewall you can specify all content type, which you cannot do with access rules.
|
Note
|
Bandwidth management policies defined with Firewall > Access Rules always have priority
over application layer bandwidth management policies. Thus, if an access rule bandwidth management policy is applied to a certain connection, then an application layer bandwidth management policy will never be applied to that connection.
|
Application Firewall allows the creation of custom email user lists as email user objects. You can only use email user objects in an SMTP client policy configuration. Email user objects can represent either individual users or the entire domain. You can also create an email user object that represents a group by adding a list of individual users to the object. This provides a way to easily include or exclude a group of users when creating an SMTP client policy. For example, you can create an email user object to represent the support group.
After you define the group in an email user object, you can create an SMTP client policy that includes or excludes the group. In the screenshot below, the settings exclude the support group from a policy that prevents executable files from being attached to outgoing email. You can use the email user object in either the MAIL FROM or RCPT TO fields of the SMTP client policy. The MAIL FROM field refers to the sender of the email. The RCPT TO field refers to the intended recipient.
Although Application Firewall cannot extract group members directly from Outlook Exchange or similar applications, you can use the member lists in Outlook to create a text file that lists the group members. Then when you create an email user object for this group, you can use the Load From File button to import the list from your text file. Be sure that each email address is on a line by itself in the text file.
The SonicOS Enhanced Application Firewall feature supports the following protocols:
|
•
|
|
•
|
|
•
|
|
•
|
You can match any protocol by creating a custom application object.
You can configure Application Firewall in the user interface of the supported SonicWALL security appliances. This section contains the following subsections:
You must enable Application Firewall before you can use it. Global settings including Enable are available on the Application Firewall > Policies page. License status is also displayed.
You can configure policies in Application Firewall using the wizard or manually. The wizard provides a safe method of configuration and helps prevent errors that could result in unnecessary blocking of network traffic. Manual configuration offers more flexibility for situations that require custom policies.
The Application Firewall > Policies page contains two global settings:
You must enable Application Firewall to activate the functionality. Application Firewall is separately licensed, and you can view the status of your license at the top of the Application Firewall > Policies page.
To enable Application Firewall and configure the global settings:
|
Step 1
|
To enable Application Firewall, select the
Enable Application Firewall
checkbox.
|
|
Step 2
|
To log all policy matches, leave the
Global Log Redundancy Filter
field set to zero. To enforce a delay between log entries for matches to the same policy, enter the number of seconds to delay.
|
Global log redundancy settings apply to all Application Firewall policies. If set to zero, a log entry is created for each policy match found in passing traffic. Other values specify the minimum number of seconds between log entries for multiple matches to the same policy. For example, a log redundancy setting of 10 will log no more than one message every 10 seconds for each policy match. Log redundancy can also be set on a per-policy basis in the Add/Edit Policy page where each individual policy configuration has its own log redundancy filter setting that can override the global log redundancy filter setting.