For information on configuring VPNs in SonicOS Enhanced, see:
For an overview of VPNs in SonicOS Enhanced, see
VPN > Settings
.
ADTRAN VPN, based on the industry-standard IPsec VPN implementation, provides a easy-to-
setup, secure solution for connecting mobile users, telecommuters, remote offices and partners via the Internet. Mobile users, telecommuters, and other remote users with broadband (DSL or cable) or dialup Internet access can securely and easily access your network resources with the ADTRAN Global VPN Client and ADTRAN GroupVPN on your ADTRAN. Remote office networks can securely connect to your network using site-to-site VPN connections that enable network-to- network VPN connections.
ADTRAN’s GroupVPN provides automatic VPN policy provisioning for ADTRAN Global VPN
Clients. The GroupVPN feature on the firewall and the ADTRAN Global VPN Client dramatically streamline VPN deployment and management. Using ADTRAN’s Client Policy Provisioning technology, you define the VPN policies for Global VPN Client users. This policy information automatically downloads from the firewall (VPN Gateway) to Global VPN Clients, saving remote users the burden of provisioning VPN connections.
You can easily and quickly create a site-to-site VPN policy or a GroupVPN policy using the
VPN
Policy Wizard
. You can also configure GroupVPN or site-to-site VPN tunnels using the Management Interface. You can define up to four GroupVPN policies, one for each zone. You can also create multiple site-to-site VPN. The maximum number of policies you can add depends on your ADTRAN model.
|
|
Note
|
Remote users must be explicitly granted access to network resources on the
Users > Local
Users
or Users > Local Groups
pages. When configuring local users or local groups, the VPN Access
tab affects the ability of remote clients using GVC connecting to GroupVPN; it
also affects
remote users using NetExtender, and SSL VPN Virtual Office bookmarks to access network resources. This is new behavior in SonicOS 5.6 and above.
To allow GVC, NetExtender, or Virtual Office users to access a network resource, the network address objects or groups must be added to the “allow” list on the VPN Access
tab.
|
Before creating or activating a VPN tunnel, gather the following information. You can print these
pages and to use as a planning checklist:

|
|
•
|
Gateway Certificate
if using 3rd part certificates. This is a certificate file you have uploaded to your firewall and plan to distribute to your VPN Clients.
|


|
|
–
|
DH Group
(if perfect forward secrecy is enabled):
|


|
|
–
|
 Always
Always
|
|
|
–
|
 DHCP Lease or Manual Configuration
DHCP Lease or Manual Configuration
|


Typically, the request for an IKE VPN SA is made from the remote site.
 Choose local network from list
(select an address object):
Choose local network from list
(select an address object):

 Local network obtains IP addresses using DHCP through this VPN Tunnel
Local network obtains IP addresses using DHCP through this VPN Tunnel
(not used with IKEv2)
 Any address
Any address
 Use this VPN Tunnel as default route for all Internet traffic
Use this VPN Tunnel as default route for all Internet traffic
 Destination network obtains IP addresses using DHCP through this VPN Tunnel
Destination network obtains IP addresses using DHCP through this VPN Tunnel
 Choose destination network from list
(select an address object):
Choose destination network from list
(select an address object):

|
|
•
|
 AES-256
AES-256
|
The settings on the responder must be the same as on the initiator except:
 Choose local network from list
(select an address object):
Choose local network from list
(select an address object):

 Local network obtains IP addresses using DHCP through this VPN Tunnel
Local network obtains IP addresses using DHCP through this VPN Tunnel
(not used with IKEv2)
 Any address
Any address
 Use this VPN Tunnel as default route for all Internet traffic
Use this VPN Tunnel as default route for all Internet traffic
 Destination network obtains IP addresses using DHCP through this VPN Tunnel
Destination network obtains IP addresses using DHCP through this VPN Tunnel
 Choose destination network from list
(select an address object):
Choose destination network from list
(select an address object):

The
VPN Policy Wizard
walks you step-by-step through the configuration of GroupVPN or site-to-site VPN policies on the firewall. After completing the configuration, the wizard creates the necessary VPN settings for the selected policy. You can use the ADTRAN Management Interface for optional advanced configuration options.
The
Global VPN Settings
section of the VPN > Settings
page displays the following information:
|
|
•
|
Enable VPN
must be selected to allow VPN policies through the ADTRAN security policies.
|
|
|
•
|
Unique Firewall Identifier
- the default value is the serial number of the ADTRAN. You can change the Identifier, and use it for configuring VPN tunnels.
|
All existing VPN policies are displayed in the
VPN Policies
table. Each entry displays the following information:
|
|
•
|
Name
:
Displays the default name or user-defined VPN policy name.
|
|
|
•
|
Gateway
: Displays the IP address of the remote ADTRAN. If 0.0.0.0 is used, no Gateway is displayed.
|
|
|
•
|
Destinations
: Displays the IP addresses of the destination networks.
|
|
|
•
|
Crypto Suite
: Displays the type of encryption used for the VPN policy.
|
|
|
•
|
Enable
: Selecting the check box enables the VPN Policy. Clearing the check box disables it.
|
|
|
•
|
Configure
: Clicking the Edit icon allows you to edit the VPN policy. Clicking the Delete  icon allows you to delete the VPN policy. The predefined GroupVPN policies cannot be deleted, so the Delete icons are dimmed. GroupVPN policies also have a Disk
icon for exporting the VPN policy configuration as a file for local installation by ADTRAN Global VPN Clients. icon allows you to delete the VPN policy. The predefined GroupVPN policies cannot be deleted, so the Delete icons are dimmed. GroupVPN policies also have a Disk
icon for exporting the VPN policy configuration as a file for local installation by ADTRAN Global VPN Clients.
|
The number of VPN policies defined, policies enabled, and the maximum number of Policies
allowed is displayed below the table. You can define up to 4 GroupVPN policies, one for each zone. These GroupVPN policies are listed by default in the VPN Policies table as WAN
GroupVPN
, LAN GroupVPN
, DMZ GroupVPN
, and WLAN GroupVPN
. Clicking on the edit icon in the Configure column for the GroupVPN displays the VPN Policy
window for configuring the GroupVPN policy.
Below the VPN Policies table are the following buttons:
|
|
•
|
Add
- Accesses the VPN Policy
window to configure site-to-site VPN policies.
|
|
|
•
|
Delete
- Deletes the selected (checked box before the VPN policy name in the Name
column. You cannot delete the GroupVPN policies.
|
|
|
•
|
Delete All
- Deletes all VPN policies in the VPN Policies table except the default GroupVPN policies.
|
The
VPN Policies
table provides easy pagination for viewing a large number of VPN policies. You can navigate a large number of VPN policies listed in the VPN Policies
table by using the navigation control bar located at the top right of the VPN Policies
table. Navigation control bar includes four buttons. The far left button displays the first page of the table. The far right button displays the last page. The inside left and right arrow buttons moved the previous or next page respectively.
You can enter the policy number (the number listed before the policy name in the
# Name
column) in the Items
field to move to a specific VPN policy. The default table configuration displays 50 entries per page. You can change this default number of entries for tables on the System > Administration
page.
You can sort the entries in the table by clicking on the column header. The entries are sorted
by ascending or descending order. The arrow to the right of the column entry indicates the sorting status. A down arrow means ascending order. An up arrow indicates a descending order.
A list of currently active VPN tunnels is displayed in this section. The table lists the name of the
VPN Policy, the local LAN IP addresses, and the remote destination network IP addresses as well as the peer gateway IP address.
Click the
Renegotiate
button to force the VPN Client to renegotiate the VPN tunnel.
In the Currently Active VPN Tunnels table, click on the Statistics icon in the row for a tunnel to
view the statistics on that tunnel. The VPN Tunnel Statistics icon displays:
|
|
•
|
Create Time
: The date and time the tunnel came into existence.
|
|
|
•
|
Packets In
: The number of packets received from this tunnel.
|
|
|
•
|
Packets Out
: The number of packets sent out from this tunnel.
|
|
|
•
|
Bytes In
: The number of bytes received from this tunnel.
|
|
|
•
|
Bytes Out
: The number of bytes sent out from this tunnel.
|
For detailed information on configuring VPNs in SonicOS Enhanced, see:
ADTRAN
GroupVPN
facilitates the set up and deployment of multiple ADTRAN Global VPN Clients by the firewall administrator. GroupVPN
is only available for ADTRAN Global VPN Clients and it is recommended you use XAUTH/RADIUS or third party certificates in conjunction with the Group VPN
for added security.
For more information on the ADTRAN Global VPN Client, see the
ADTRAN Global VPN Client
Administrator’s Guide
.
The default GroupVPN configuration allows you to support ADTRAN Global VPN Clients
without any further editing of the VPN policy, except to check the Enable
box for GroupVPN in the VPN Policies
table.
ADTRAN supports four GroupVPN policies. You can create GroupVPN policies for the DMZ,
LAN, WAN, and WLAN zones. These GroupVPN policies are listed in the VPN policies tables as WAN Group VPN
, LAN GroupVPN
, DMZ GroupVPN
, and WLAN GroupVPN
. For these GroupVPN policies, you can choose from IKE using Preshared Secret
or IKE using 3rd Party
Certificates
for your IPsec Keying Mode.
SonicOS supports the creation and management of IPsec VPNs.
To configure the WAN GroupVPN, follow these steps:
|
Step 1
|
Click the
edit
icon for the WAN
GroupVPN
entry. The VPN Policy
window is displayed.
|
|
Step 2
|
In the
General
tab, IKE using Preshared Secret
is the default setting for Authentication
Method
. A Shared Secret is automatically generated by the firewall in the Shared
Secret
field, or you can generate your own shared secret. Shared Secrets
must be minimum of four characters. You cannot change the name of any GroupVPN policy.
|
|
Step 3
|
Click the
Proposals
tab to continue the configuration process.
|
|
Step 4
|
In the
IKE (Phase 1) Proposal
section, use the following settings:
|
|
|
–
|
Select
3DES
, AES-128
, or AES-256
from the Encryption
menu.
|
|
|
–
|
Enter a value in the
Life Time (seconds)
field. The default setting of 28800
forces the tunnel to renegotiate and exchange keys every 8 hours.
|
|
Step 5
|
In the
IPsec (Phase 2) Proposal
section, select the following settings:
|
|
|
–
|
Select
3DES
, AES-128
, or AES-256
from the Encryption
menu.
|
|
|
–
|
Select
Enable Perfect Forward Secrecy
if you want an additional Diffie-Hellman key exchange as an added layer of security. Select Group 2
from the DH Group
menu.
|
|
|
–
|
Enter a value in the
Life Time (seconds)
field. The default setting of 28800
forces the tunnel to renegotiate and exchange keys every 8 hours.
|
|
|
–
|
Enable Multicast
- Enables IP multicasting traffic, such as streaming audio (including VoIP) and video applications, to pass through the VPN tunnel.
|
|
|
–
|
Management via this SA
: - If using the VPN policy to manage the firewall, select the management method, either HTTP
or HTTPS
.
|
|
|
–
|
Default Gateway
- Allows the network administrator to specify the IP address of the default network route for incoming IPsec packets for this VPN policy. Incoming packets are decoded by the ADTRAN and compared to static routes configured in the firewall. Since packets can have any IP address destination, it is impossible to configure enough static routes to handle the traffic. For packets received via an IPsec tunnel, the ADTRAN looks up a route. If no route is found, the security appliance checks for a Default Gateway. If a Default Gateway is detected, the packet is routed through the gateway. Otherwise, the packet is dropped.
|
|
|
–
|
Require Authentication of VPN Clients via XAUTH
- Requires that all inbound traffic on this VPN tunnel is from an authenticated user. Unauthenticated traffic is not allowed on the VPN tunnel. he Trusted users
group is selected by default. You can select another user group or Everyone
from User Group for XAUTH users
.
|
|
|
–
|
Allow Unauthenticated VPN Client Access
- Allows you to enable unauthenticated VPN client access. If you uncheck Require Authentication of VPN Clients via
XAUTH
, the Allow Unauthenticated VPN Client Access
menu is activated. Select an Address Object or Address Group from menu of predefined options, or select Create
new address object
or Create new address group
to create a new one.
|
|
Step 8
|
Click the
Client
tab, select any of the following settings you want to apply to your GroupVPN policy.
|
|
|
•
|
Never
- Global VPN Client is not allowed to cache the username and password. The user will be prompted for a username and password when the connection is enabled, and also every time there is an IKE Phase 1 rekey.
|
|
|
•
|
Single Session
- Global VPN Client user prompted for username and password each time the connection is enabled and will be valid until the connection is disabled. The username and password is used through IKE Phase 1 rekey.
|
|
|
•
|
Always
- Global VPN Client user prompted for username and password only once when connection is enabled. When prompted, the user will be given the option of caching the username and password.
|
|
|
–
|
Virtual Adapter Settings
- The use of the Virtual Adapter by the Global VPN Client (GVC) is dependent upon a DHCP server, either the internal SonicOS or a specified external DHCP server, to allocate addresses to the Virtual Adapter. In instances where predictable addressing was a requirement, it is necessary to obtain the MAC address of the Virtual Adapter, and to create a DHCP lease reservation. To reduce the administrative burden of providing predictable Virtual Adapter addressing, you can configure the GroupVPN to accept static addressing of the Virtual Adapter's IP configuration. This feature requires the use of GVC version 3.0 or later.
|
|
|
•
|
None
- A Virtual Adapter will not be used by this GroupVPN connection.
|
|
|
•
|
DHCP Lease
- The Virtual Adapter will obtain its IP configuration from the DHCP Server only, as configure in the VPN > DHCP over VPN
page.
|
|
|
•
|
DHCP Lease or Manual Configuration
- When the GVC connects to the ADTRAN, the policy from the ADTRAN instructs the GVC to use a Virtual Adapter, but the DHCP messages are suppressed if the Virtual Adapter has been manually configured. The configured value is recorded by the ADTRAN so that it can proxy ARP for the manually assigned IP address. By design, there are currently no limitations on IP address assignments for the Virtual Adapter. Only duplicate static addresses are not permitted.
|
|
|
–
|
Allow Connections to
- Client network traffic matching destination networks of each gateway is sent through the VPN tunnel of that specific gateway.
|
|
|
•
|
This Gateway Only
- Allows a single connection to be enabled at a time. Traffic that matches the destination networks as specified in the policy of the gateway is sent through the VPN tunnel. If this option is selected along with Set Default Route as this Gateway, then the Internet traffic is also sent through the VPN tunnel. If this option is selected without selecting Set Default Route as this Gateway, then the Internet traffic is blocked.
|
|
|
•
|
All Secured Gateways
- Allows one or more connections to be enabled at the same time. Traffic matching the destination networks of each gateway is sent through the VPN tunnel of that specific gateway. If this option is selected along with Set Default Route as this Gateway
, then Internet traffic is also sent through the VPN tunnel. If this option is selected without Set Default Route as this Gateway
, then the Internet traffic is blocked. Only one of the multiple gateways can have Set
Default Route as this Gateway
enabled.
|
|
|
•
|
Split Tunnels
- Allows the VPN user to have both local Internet connectivity and VPN connectivity.
|
|
|
–
|
Set Default Route as this Gateway
- Enable this check box if all remote VPN connections access the Internet through this VPN tunnel. You can only configure one VPN policy to use this setting.
|
To configure GroupVPN with IKE using 3rd Party Certificates, follow these steps:
|
Step 1
|
In the
VPN > Settings
page click the edit icon under Configure
. The VPN Policy
window is displayed.
|
|
Step 2
|
In the
Security Policy
section, select IKE using 3rd Party Certificate
s from the Authentication Method
menu. The VPN policy name is GroupVPN
by default and cannot be changed.
|
|
|
–
|
E-Mail ID and Domain Name
- The Email ID
and Domain Name
types are based on the certificate's Subject Alternative Name field, which is not contained in all certificates by default. If the certificate does not contain a Subject Alternative Name field, this filter will not work. The E-Mail ID
and Domain Name
filters can contain a string or partial string identifying the acceptable range required. The strings entered are not case sensitive and can contain the wild card characters * (for more than 1 character) and ? (for a single character). For example, the string *@adtran.com when E-Mail ID
is selected, would allow anyone with an email address that ended in www.adtran.com to have access; the string *sv.us.www.adtran.com when Domain Name is selected, would allow anyone with a domain name that ended in sv.us.www.adtran.com to have access.
|
|
|
–
|
Distinguished Name
- based on the certificates Subject Distinguished Name field, which is contained in all certificates by default. The format of any Subject Distinguished Name is determined by the issuing Certificate Authority. Common fields are Country (C=), Organization (O=), Organizational Unit (OU=), Common Name (CN=), Locality (L=), and vary with the issuing Certificate Authority. The actual Subject Distinguished Name field in an X.509 Certificate is a binary object which must be converted to a string for matching purposes. The fields are separated by the forward slash character, for example: /C=US/O=ADTRAN, Inc./OU=TechPubs/CN=Joe Pub
|
Up to three organizational units can be specified. The usage is
c=*;o=*;ou=*;ou=*;ou=*;cn=*. The final entry does not need to contain a semi-colon. You must enter at least one entry, i.e. c=us.
|
Step 6
|
Check
Allow Only Peer Certificates Signed by Gateway Issuer
to specify that peer certificates must be signed by the issuer specified in the Gateway Certificate
menu.
|
|
Step 8
|
In the
IKE (Phase 1) Proposal
section, select the following settings:
|
|
|
–
|
Select
3DES
, AES-128
, or AES-256
from the Encryption
menu.
|
|
|
–
|
Enter a value in the
Life Time (seconds)
field. The default setting of 28800
forces the tunnel to renegotiate and exchange keys every 8 hours.
|
|
Step 9
|
In the
IPsec (Phase 2) Proposal
section, select the following settings:
|
|
|
–
|
Select
3DES
, AES-128
, or AES-256
from the Encryption
menu.
|
|
|
–
|
Select
Enable Perfect Forward Secrecy
if you want an additional Diffie-Hellman key exchange as an added layer of security. Select Group 2
from the DH Group
menu.
|
|
|
–
|
Enter a value in the
Life Time (seconds)
field. The default setting of 28800
forces the tunnel to renegotiate and exchange keys every 8 hours.
|
|
Step 10
|
Click on the
Advanced
tab and select any of the following optional settings that you want to apply to your GroupVPN Policy:
|
|
|
–
|
Enable Multicast
- Enables IP multicasting traffic, such as streaming audio (including VoIP) and video applications, to pass through the VPN tunnel.
|
|
|
–
|
Management via this SA
- If using the VPN policy to manage the firewall, select the management method, either HTTP
or HTTPS
.
|
|
|
–
|
Default Gateway
- Used at a central site in conjunction with a remote site using the Route all Internet traffic through this SA
check box. Default LAN Gateway allows the network administrator to specify the IP address of the default LAN route for incoming IPsec packets for this SA. Incoming packets are decoded by the ADTRAN and compared to static routes configured in the ADTRAN. Since packets can have any IP address destination, it is impossible to configure enough static routes to handle the traffic. For packets received via an IPsec tunnel, the ADTRAN looks up a route for the LAN. If no route is found, the ADTRAN checks for a Default LAN Gateway. If a Default LAN Gateway is detected, the packet is routed through the gateway. Otherwise, the packet is dropped.
|
|
Step 11
|
Click on the
Client
tab and select any of the following boxes that you want to apply to Global VPN Client provisioning:
|
|
|
•
|
Never
- Global VPN Client is not allowed to cache username and password. The user will be prompted for a username and password when the connection is enabled and also every time there is an IKE phase 1 rekey.
|
|
|
•
|
Single Session
- The user will be prompted for username and password each time the connection is enabled and will be valid until the connection is disabled. This username and password is used through IKE phase 1 rekey.
|
|
|
•
|
Always
- The user will be prompted for username and password only once when connection is enabled. When prompted, the user will be given the option of caching the username and password.
|
|
|
–
|
Virtual Adapter Settings
- The use of the Virtual Adapter by the Global VPN Client (GVC) is dependent upon a DHCP server, either the internal SonicOS or a specified external DHCP server, to allocate addresses to the Virtual Adapter. In instances where predictable addressing was a requirement, it is necessary to obtain the MAC address of the Virtual Adapter, and to create a DHCP lease reservation. To reduce the administrative burden of providing predictable Virtual Adapter addressing, you can configure the GroupVPN to accept static addressing of the Virtual Adapter's IP configuration. This feature requires the use of GVC version 3.0 or later.
|
|
|
•
|
None
- A Virtual Adapter will not be used by this GroupVPN connection.
|
|
|
•
|
DHCP Lease
- The Virtual Adapter will obtain its IP configuration from the DHCP Server only, as configure in the VPN > DHCP over VPN
page.
|
|
|
•
|
DHCP Lease or Manual Configuration
- When the GVC connects to the ADTRAN, the policy from the ADTRAN instructs the GVC to use a Virtual Adapter, but the DHCP messages are suppressed if the Virtual Adapter has been manually configured. The configured value is recorded by the ADTRAN so that it can proxy ARP for the manually assigned IP address. By design, there are currently no limitations on IP address assignments for the Virtual Adapter. Only duplicate static addresses are not permitted.
|
|
|
–
|
Allow Connections to
- Client network traffic matching destination networks of each gateway is sent through the VPN tunnel of that specific gateway.
|
|
|
•
|
This Gateway Only
- Allows a single connection to be enabled at a time. Traffic that matches the destination networks as specified in the policy of the gateway is sent through the VPN tunnel. If this option is selected along with Set Default Route as this Gateway, then the Internet traffic is also sent through the VPN tunnel. If this option is selected without selecting Set Default Route as this Gateway, then the Internet traffic is blocked.
|
|
|
•
|
All Secured Gateways
- Allows one or more connections to be enabled at the same time. Traffic matching the destination networks of each gateway is sent through the VPN tunnel of that specific gateway. If this option is selected along with Set Default Route as this Gateway
, then Internet traffic is also sent through the VPN tunnel. If this option is selected without Set Default Route as this Gateway
, then the Internet traffic is blocked. Only one of the multiple gateways can have Set
Default Route as this Gateway
enabled.
|
|
|
•
|
Split Tunnels
- Allows the VPN user to have both local Internet connectivity and VPN connectivity.
|
|
|
–
|
Set Default Route as this Gateway
- Enable this check box if all remote VPN connections access the Internet through this SA. You can only configure one SA to use this setting.
|
If you want to export the Global VPN Client configuration settings to a file for users to import
into their Global VPN Clients, follow these instructions:
|
Step 1
|
Click the
Disk
icon in the Configure
column for the GroupVPN entry in the VPN Policies
table. The Export VPN Client Policy
window appears.
|
|
Step 3
|
Click
Yes
. The VPN Policy Export
window appears.
|
|
Step 4
|
Type a password in the
Passwor
d field and reenter it in the Confirm Password
field, if you want to encrypt the exported file. If you choose not to enter a password, the exported file is not encrypted.
|
|
Step 5
|
Click
Submit
. If you did not enter a password, a message appears confirming your choice.
|
|
Step 6
|
Click
OK
. You can change the configuration file before saving.
|
The file can be saved to a floppy disk or sent electronically to remote users to configure their
Global VPN Clients.
When designing VPN connections, be sure to document all pertinent IP addressing information
and create a network diagram to use as a reference. A sample planning sheet is provided on the next page. The ADTRAN must have a routable WAN IP address whether it is dynamic or static. In a VPN network with dynamic and static IP addresses, the VPN gateway with the dynamic address must initiate the VPN connection.
Site-to-Site VPN configurations can include the following options:
|
|
•
|
Branch Office (Gateway to Gateway)
- A ADTRAN is configured to connect to another ADTRAN via a VPN tunnel. Or, a ADTRAN is configured to connect via IPsec to another manufacturer’s firewall.
|
|
|
•
|
Hub and Spoke Design
- All ADTRAN VPN gateways are configured to connect to a central ADTRAN (hub), such as a corporate ADTRAN. The hub must have a static IP address, but the spokes can have dynamic IP addresses. If the spokes are dynamic, the hub must be a ADTRAN.
|
|
|
•
|
Mesh Design
- All sites connect to all other sites. All sites must have static IP addresses.
|
See
“
Planning Your VPN
”
for a planning sheet to help you set up your VPN.
You can create or modify existing VPN policies using the VPN Policy window. Clicking the
Add
button under the VPN Policies
table displays the VPN Policy
window for configuring the following IPsec Keying mode VPN policies:
This section also contains information on configuring a static route to act as a failover in case
the VPN tunnel goes down. See “
Configuring VPN Failover to a Static Route
”
for more information.
To configure a VPN Policy using Internet Key Exchange (IKE), follow the steps below:
|
Step 1
|
Click
Add
on the VPN > Settings
page. The VPN Policy
window is displayed.
|
|
Step 2
|
In the
General
tab, select IKE using Preshared Secret
from the Authentication Method
menu.
|
Optionally, specify a
Local IKE ID (optional)
and Peer IKE ID (optional)
for this Policy. By default, the IP Address
(ID_IPv4_ADDR) is used for Main Mode negotiations, and the ADTRAN Identifier (ID_USER_FQDN) is used for Aggressive Mode.
|
Step 8
|
Under
Local Networks
, select a local network from Choose local network from list
if a specific local network can access the VPN tunnel. If hosts on this side of the VPN connection will be obtaining their addressing from a DHCP server on the remote side of the tunnel, select Local network obtains IP addresses using DHCP through this VPN tunnel
. If traffic can originate from any local network, select Any Address
. Use this option if a peer has Use this
VPN tunnel as default route for all Internet traffic
selected.
|
|
Step 9
|
Under
Destination Networks
, select Use this VPN Tunnel as default route for all Internet
traffic
if traffic from any local user cannot leave the firewall unless it is encrypted. You can only configure one SA to use this setting. If the remote side of this VPN connection is be obtaining its addressing from a DHCP server on this side of the tunnel, select Destination network
obtains IP addresses using DHCP server through this tunnel
. Alternatively, select Choose
Destination network from list
, and select the address object or group.
|
|
Step 10
|
Click
Proposals
.
|
|
Step 11
|
Under
IKE (Phase 1) Proposal
, select either Main Mode
, Aggressive Mode
, or IKEv2
from the Exchange
menu. Aggressive Mode
is generally used when WAN addressing is dynamically assigned. IKEv2
causes all the negotiation to happen via IKE v2 protocols, rather than using IKE Phase 1 and Phase 2. If you use IKE v2, both ends of the VPN tunnel must use IKE v2.
|
|
Step 12
|
Under
IKE (Phase 1) Proposal
, the default values for DH Group
, Encryption
, Authentication
, and Life Time
are acceptable for most VPN configurations. Be sure the Phase 1 values on the opposite side of the tunnel are configured to match. You can also choose AES-
128
, AES-192
, or AES-256
from the Authentication
menu instead of 3DES for enhanced authentication security.
|
|
Step 13
|
Under IPsec (Phase 2) Proposal
, the default values for Protocol
, Encryption
, Authentication
, Enable Perfect Forward Secrecy
, DH Group
, and Lifetime
are acceptable for most VPN SA configurations. Be sure the Phase 2 values on the opposite side of the tunnel are configured to match.
|
|
Step 14
|
Click the
Advanced
tab and select any of the following optional settings you want to apply to your VPN policy:
|
|
|
•
|
Select
Enable Keep Alive
to use heartbeat messages between peers on this VPN tunnel. If one end of the tunnel fails, using Keepalives will allow for the automatic renegotiation of the tunnel once both sides become available again without having to wait for the proposed Life Time to expire.
|
|
|
•
|
The
Suppress automatic Access Rules creation for VPN Policy
setting is not enabled by default to allow the VPN traffic to traverse the appropriate zones.
|
|
|
•
|
Select
Enable Windows Networking (NetBIOS) Broadcast
to allow access to remote network resources by browsing the Windows® Network Neighborhood.
|
|
|
•
|
Select
Enable Multicast
to allow IP multicasting traffic, such as streaming audio (including VoIP) and video applications, to pass through the VPN tunnel.
|
|
|
•
|
Select
Apply NAT Policies
if you want the ADTRAN to translate the Local, Remote or both networks communicating via this VPN tunnel. To perform Network Address Translation on the Local Network, select or create an Address Object in the Translated Local Network
menu. To translate the Remote Network, select or create an Address Object in the Translated Remote Network
menu. Generally, if NAT is required on a tunnel, either Local or Remote should be translated, but not both. Apply NAT Policies
is particularly useful in cases where both sides of a tunnel use either the same or overlapping subnets.
|
|
|
•
|
Select an interface or zone from the
VPN Policy bound to
menu. A Zone WAN
is the preferred selection if you are using WAN Load Balancing and you wish to allow the VPN to use either WAN interface.
|
|
|
•
|
Select
Enable Keep Alive
to use heartbeat messages between peers on this VPN tunnel. If one end of the tunnel fails, using Keepalives will allow for the automatic renegotiation of the tunnel once both sides become available again without having to wait for the proposed Life Time to expire.
|
|
|
•
|
Select
Suppress automatic Access Rules creation for VPN Policy
to turn off the automatic access rules created between the LAN and VPN zones for this VPN policy.
|
|
|
•
|
Select
Enable Windows Networking (NetBIOS) Broadcast
to allow access to remote network resources by browsing the Windows® Network Neighborhood.
|
|
|
•
|
Select
Enable Multicast
to allow IP multicasting traffic, such as streaming audio (including VoIP) and video applications, to pass through the VPN tunnel.
|
|
|
•
|
Select
Apply NAT Policies
if you want the ADTRAN to translate the Local, Remote or both networks communicating via this VPN tunnel. To perform Network Address Translation on the Local Network, select or create an Address Object in the Translated Local Network
menu. To translate the Remote Network, select or create an Address Object in the Translated Remote Network
menu. Generally, if NAT is required on a tunnel, either Local or Remote should be translated, but not both. Apply NAT Policies
is particularly useful in cases where both sides of a tunnel use either the same or overlapping subnets.
|
|
|
•
|
Enter the
Default LAN Gateway
if you have more than one gateway and you want this one always to be used first.
|
|
|
•
|
Select an interface or zone from the
VPN Policy bound to
menu. A Zone WAN
is the preferred selection if you are using WAN Load Balancing and you wish to allow the VPN to use either WAN interface.
|
|
|
•
|
Under
IKEv2
Settings (visible only if you selected IKEv2
for Exchange
on the Proposals
tab), The Do not send trigger packet during IKE SA negotiation
checkbox is cleared by default and should only be selected when required for interoperability.
|
The term
Trigger Packet
refers to the use of initial Traffic Selector
payloads populated with the IP addresses from the packet that caused SA negotiation to begin. It is recommended practice to include Trigger Packets
to assist the IKEv2 Responder in selecting the correct protected IP address ranges from its Security Policy Database. Not all implementations support this feature, so it may be appropriate to disable the inclusion of Trigger Packets
to some IKE peers.
To manually configure a VPN policy between two ADTRAN appliances using Manual Key,
follow the steps below:
|
Step 1
|
Click
Add
on the VPN > Settings
page. The VPN Policy
window is displayed.
|
|
Step 2
|
In the
General
tab of the VPN Policy
window, select Manual Key
from the IPsec Keying Mode
menu. The VPN Policy
window displays the manual key options.
|
|
Step 6
|
Select a local network from
Choose local network from list
if a specific local network can access the VPN tunnel. If traffic can originate from any local network, select Any
Address
. Use this option is a peer has Use this VPN Tunnel as default route for all Internet traffic
selected. You can only configure one SA to use this setting. Alternatively, select Choose
Destination network from list
, and select the address object or group.
|
|
Step 8
|
Define an
Incoming SPI
and an Outgoing SPI
. The SPIs are hexadecimal (0123456789abcedf) and can range from 3 to 8 characters in length.
|
|
Step 9
|
The default values for
Protocol
, Phase 2 Encryption
, and Phase 2 Authentication
are acceptable for most VPN SA configurations.
|
|
|
Note
|
The values for
Protocol
, Phase 2 Encryption
, and Phase 2 Authentication
must match the values on the remote ADTRAN.
|
|
|
Tip
|
Valid hexadecimal characters include 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, a, b, c, d, e, and f.
1234567890abcdef is an example of a valid DES or ARCFour encryption key. If you enter an incorrect encryption key, an error message is displayed at the bottom of the browser window.
|
|
Step 12
|
Click the
Advanced
tab and select any of the following optional settings you want to apply to your VPN policy.
|
|
|
–
|
The
Suppress automatic Access Rules creation for VPN Policy
setting is not enabled by default to allow the VPN traffic to traverse the appropriate zones.
|
|
|
–
|
Select
Enable Windows Networking (NetBIOS) broadcast
to allow access to remote network resources by browsing the Windows® Network Neighborhood.
|
|
|
–
|
Select
Apply NAT Policies
if your want the ADTRAN to translate the Local, Remote or both networks communicating via this VPN tunnel. To perform Network Address Translation on the Local Network, select or create an Address Object in the Translated
Local Network
drop-down box. To translate the Remote Network, select or create an Address Object in the Translated Remote Network
drop-down box. Generally, if NAT is required on a tunnel, either Local or Remote should be translated, but not both. Apply NAT Policies
is particularly useful in cases where both sides of a tunnel use either the same or overlapping subnets.
|
|
|
–
|
Select
HTTP
, HTTPS
, or both in the User login via this SA
to allow users to login using the SA.
|
|
Step 14
|
Click
Accept
on the VPN > Settings
page to update the VPN Policies.
|
|
Step 1
|
Click
Add
on the VPN > Settings
page. The VPN Policy
window is displayed.
|
|
Step 2
|
In the
General
tab, select Manual Key
from the IPsec Keying Mode
menu.
|
|
Step 6
|
Select a local network from
Choose local network from list
if a specific local network can access the VPN tunnel. If traffic can originate from any local network, select Any
Address
. Select Use this VPN Tunnel as default route for all Internet traffic
if traffic from any local user cannot leave the firewall unless it is encrypted. You can only configure one SA to use this setting. Alternatively, select Choose Destination network from list
, and select the address object or group.
|
|
Step 8
|
Define an
Incoming SPI
and an Outgoing SPI
. The SPIs are hexadecimal (0123456789abcedf) and can range from 3 to 8 characters in length.
|
|
Step 9
|
The default values for
Protocol
, Phase 2 Encryption
, and Phase 2 Authentication
are acceptable for most VPN SA configurations.
|
|
|
Note
|
The values for
Protocol
, Phase 2 Encryption
, and Phase 2 Authentication
must match the values on the remote ADTRAN.
|
|
|
Tip
|
Valid hexadecimal characters include 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, a, b, c, d, e, and f.
1234567890abcdef is an example of a valid DES or ARCFour encryption key. If you enter an incorrect encryption key, an error message is displayed at the bottom of the browser window.
|
|
Step 12
|
Click the
Advanced
tab and select any of the following optional settings you want to apply to your VPN policy:
|
|
|
–
|
The
Suppress automatic Access Rules creation for VPN Policy
setting is not enabled by default to allow the VPN traffic to traverse the appropriate zones.
|
|
|
–
|
Select
Enable Windows Networking (NetBIOS) broadcast
to allow access to remote network resources by browsing the Windows® Network Neighborhood.
|
|
|
–
|
Select
Apply NAT Policies
if you want the ADTRAN to translate the Local, Remote or both networks communicating via this VPN tunnel. To perform Network Address Translation on the Local Network, select or create an Address Object in the Translated
Local Network
drop-down box. To translate the Remote Network, select or create an Address Object in the Translated Remote Network
drop-down box. Generally, if NAT is required on a tunnel, either Local or Remote should be translated, but not both. Apply NAT Policies
is particularly useful in cases where both sides of a tunnel use either the same or overlapping subnets.
|
|
|
–
|
Select
HTTP
, HTTPS
, or both in the User login via this SA
to allow users to login using the SA.
|
|
Step 14
|
Click
Accept
on the VPN > Settings
page to update the VPN Policies.
|
To create a VPN SA using IKE and third party certificates, follow these steps:
|
Step 1
|
In the
VPN > Settings
page, click Add
. The VPN Policy
window is displayed.
|
|
Step 2
|
In the
Authentication Method
list in the General
tab, select IKE using 3rd Party
Certificates
.The VPN Policy
window displays the 3rd party certificate options.
|
|
Step 5
|
Under
IKE Authentication
, select a third party certificate from the Local Certificate
list. You must have imported local certificates before selecting this option.
|
|
|
–
|
E-Mail ID
and Domain Name
- The Email ID
and Domain Name
types are based on the certificate's Subject Alternative Name field, which is not contained in all certificates by default. If the certificate contains a Subject Alternative Name, that value must be used. For site-to-site VPNs, wild card characters (such as * for more than 1 character or ? for a single character) cannot be used. The full value of the E-Mail ID or Domain Name must be entered. This is because site-to-site VPNs are expected to connect to a single peer, as opposed to Group VPNs, which expect multiple peers to connect.
|
|
|
–
|
Distinguished Name
- Based on the certificates Subject Distinguished Name field, which is contained in all certificates by default. As with the E-Mail ID and Domain Name above, the entire Distinguished Name field must be entered for site-to-site VPNs Wild card characters are not supported.
|
The format of any Subject Distinguished Name is determined by the issuing Certificate
Authority. Common fields are Country (C=), Organization (O=), Organizational Unit (OU=), Common Name (CN=), Locality (L=), and vary with the issuing Certificate Authority. The actual Subject Distinguished Name field in an X.509 Certificate is a binary object which must be converted to a string for matching purposes. The fields are separated by the forward slash character, for example: /C=US/O=ADTRAN, Inc./
OU=TechPubs/CN=Joe Pub
To find the certificate details (Subject Alternative Name, Distinguished Name, etc.),
navigate to the System > Certificates
page and click on the  Export button for the certificate.
Export button for the certificate.
|
Step 9
|
Under
Local Networks
, select a local network from Choose local network from list
if a specific local network can access the VPN tunnel. If hosts on this side of the VPN connection will be obtaining their addressing from a DHCP server on the remote side of the tunnel, select Local network obtains IP addresses using DHCP through this VPN tunnel
. If traffic can originate from any local network, select Any Address
.
|
|
Step 10
|
Under
Destination Networks
, select Use this VPN Tunnel as default route for all Internet
traffic
if traffic from any local user cannot leave the firewall unless it is encrypted. You can only configure one SA to use this setting. If the remote side of this VPN connection is be obtaining its addressing from a DHCP server on this side of the tunnel, select Destination network
obtains IP addresses using DHCP server through this tunnel
. Alternatively, select Choose
Destination network from list
, and select the address object or group.
|
|
Step 12
|
In the
IKE (Phase 1) Proposal
section, select the following settings:
|
|
|
–
|
Select
Main Mode
or Aggressive Mode
from the Exchange menu.
|
|
|
–
|
Select
3DES
, AES-128
, AES-192
, or AES-256
from the Encryption
menu.
|
|
|
–
|
Enter a value in the
Life Time (seconds)
field. The default setting of 28800
forces the tunnel to renegotiate and exchange keys every 8 hours.
|
|
Step 13
|
In the
IPsec (Phase 2) Proposal
section, select the following settings:
|
|
|
–
|
Select
3DES
, AES-128
, AES-192
, or AES-256
from the Encryption
menu.
|
|
|
–
|
Select
Enable Perfect Forward Secrecy
if you want an additional Diffie-Hellman key exchange as an added layer of security. Select Group 2
from the DH Group
menu.
|
|
|
–
|
Enter a value in the
Life Time (seconds)
field. The default setting of 28800
forces the tunnel to renegotiate and exchange keys every 8 hours.
|
|
Step 14
|
Click the
Advanced
tab. Select any optional configuration options you want to apply to your VPN policy:
|
|
|
–
|
Select
Enable Keep Alive
to use heartbeat messages between peers on this VPN tunnel. If one end of the tunnel fails, using Keepalives will allow for the automatic renegotiation of the tunnel once both sides become available again without having to wait for the proposed Life Time to expire.
|
|
|
–
|
The
Suppress automatic Access Rules creation for VPN Policy
setting is not enabled by default to allow the VPN traffic to traverse the appropriate zones.
|
|
|
–
|
Select
Enable Windows Networking (NetBIOS) Broadcast
to allow access to remote network resources by browsing the Windows® Network Neighborhood.
|
|
|
–
|
Select
Enable Multicast
to allow multicast traffic through the VPN tunnel.
|
|
|
–
|
Select
Apply NAT Policies
if you want the ADTRAN to translate the Local, Remote or both networks communicating via this VPN tunnel. To perform Network Address Translation on the Local Network, select or create an Address Object in the Translated
Local Network
menu. To translate the Remote Network, select or create an Address Object in the Translated Remote Network
menu. Generally, if NAT is required on a tunnel, either Local or Remote should be translated, but not both. Apply NAT Policies
is particularly useful in cases where both sides of a tunnel use either the same or overlapping subnets.
|
|
|
–
|
Select an interface or zone from the
VPN Policy bound to
menu. A zone is the preferred selection if you are using WAN Load Balancing and you wish to allow the VPN to use either WAN interface.
|
Optionally, you can configure a static route to be used as a backup route in case the VPN tunnel
goes down. The Allow VPN path to take precedence
option allows you to create a backup route for a VPN tunnel. By default, static routes have a metric of one and take precedence over VPN traffic. The Allow VPN path to take precedence
option gives precedence over the route to VPN traffic to the same destination address object. This results in the following behavior:
To configure a static route as a VPN failover, complete the following steps:
|
Step 5
|
Enable the
Allow VPN path to take precedence
checkbox.
|
For more information on configuring static routes and Policy Based Routing, see
“
Network > Routing
”
.
A policy-based approach forces the VPN policy configuration to include the network topology
configuration. This makes it difficult for the network administrator to configure and maintain the VPN policy with a constantly changing network topology.
With the Route Based VPN approach, network topology configuration is removed from the VPN
policy configuration. The VPN policy configuration creates a Tunnel Interface between two end points. Static or Dynamic routes can then be added to the Tunnel Interface. The Route Based VPN approach moves network configuration from the VPN policy configuration to Static or Dynamic Route configuration.
Not only does Route Based VPN make configuring and maintaining the VPN policy easier, a
major advantage of the Route Based VPN feature is that it provides flexibility on how traffic is routed. With this feature, users can now define multiple paths for overlapping networks over a clear or redundant VPN.
Route Based VPN configuration is a two step process. The first step involves creating a Tunnel
Interface. The crypto suites used to secure the traffic between two end-points are defined in the Tunnel Interface. The second step involves creating a static or dynamic route using Tunnel Interface.
The Tunnel Interface is created when a Policy of type “Tunnel Interface” is added for the remote
gateway. The Tunnel Interface must be bound to a physical interface and the IP address of that physical interface is used as the source address of the tunneled packet.
The following procedures explain how to add a Tunnel Interface:
|
Step 1
|
Navigate to
VPN
>Settings
>VPN Policies
. Click the Add
button. This will open the VPN Policy Configuration dialog box.
|
|
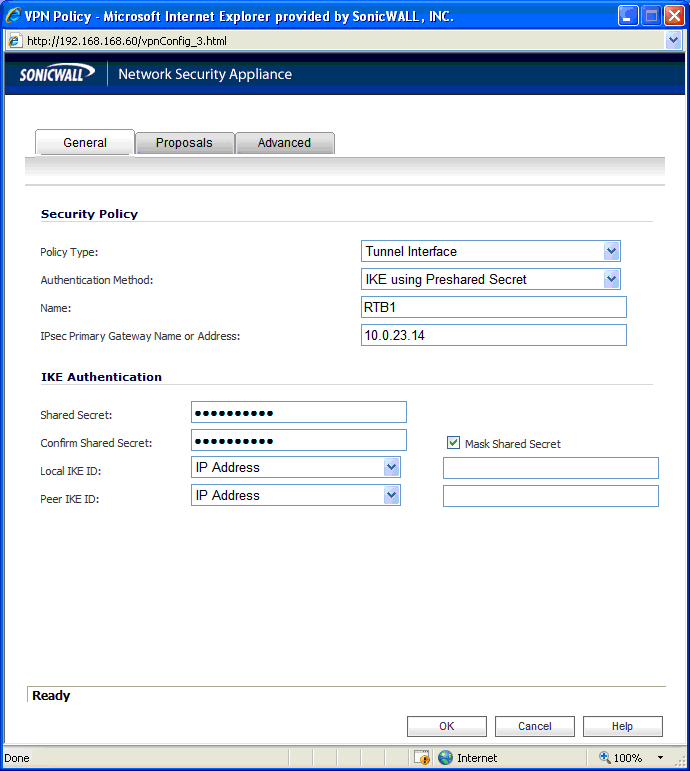
Step 2
|
On the
General
tab, select the policy type as “Tunnel Interface.”
|
|
Step 3
|
Next, navigate to the
Proposal
tab and configure the IKE and IPSec proposals for the tunnel negotiation.
|

|
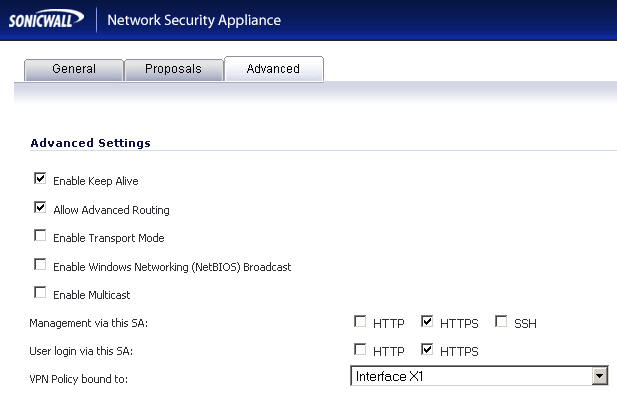
Step 4
|
Navigate to the
Advanced
tab to configure the advanced properties for the Tunnel Interface. By default, Enable Keep Alive
is enabled. This is to establish the tunnel with remote gateway proactively.
|
|
|
•
|
Allow Advanced Routing
- Adds this Tunnel Interface to the list of interfaces in the Advanced Routing table on the Network > Routing
page. By making this an optional setting, this avoids adding all Tunnel Interfaces to the Advanced Routing table, which helps streamline the routing configuration. See “
Configuring Advanced Routing for Tunnel Interfaces
”
for information on configuring RIP or OSPF advanced routing for the Tunnel Interface.
|
|
|
•
|
Enable Transport Mode
- Forces the IPsec negotiation to use Transport mode instead of Tunnel Mode. This has been introduced for compatibility with Nortel. When this option is enabled on the local firewall, it MUST be enabled on the remote firewall as well for the negotiation to succeed.
|
|
|
•
|
VPN Policy bound to
- Sets the interface the Tunnel Interface is bound to. This is x1 by default.
|
After you have successfully added a Tunnel Interface, you may then create a Static Route.
Follow the procedures to create a Static Route for a Tunnel Interface:
Navigate to
Network
>Routing
>Route Policies
. Click the Add
button. A dialogue window appears for adding Static Route. Note that the “Interface” dropdown menu lists all available tunnel interfaces.

After a tunnel interface is created, multiple route entries can be configured to use the same
tunnel interface for different networks. This provides a mechanism to modify the network topology without making any changes to the tunnel interface.
The image below shows an example of same tunnel interface for different networks (Routes 1
& 2):
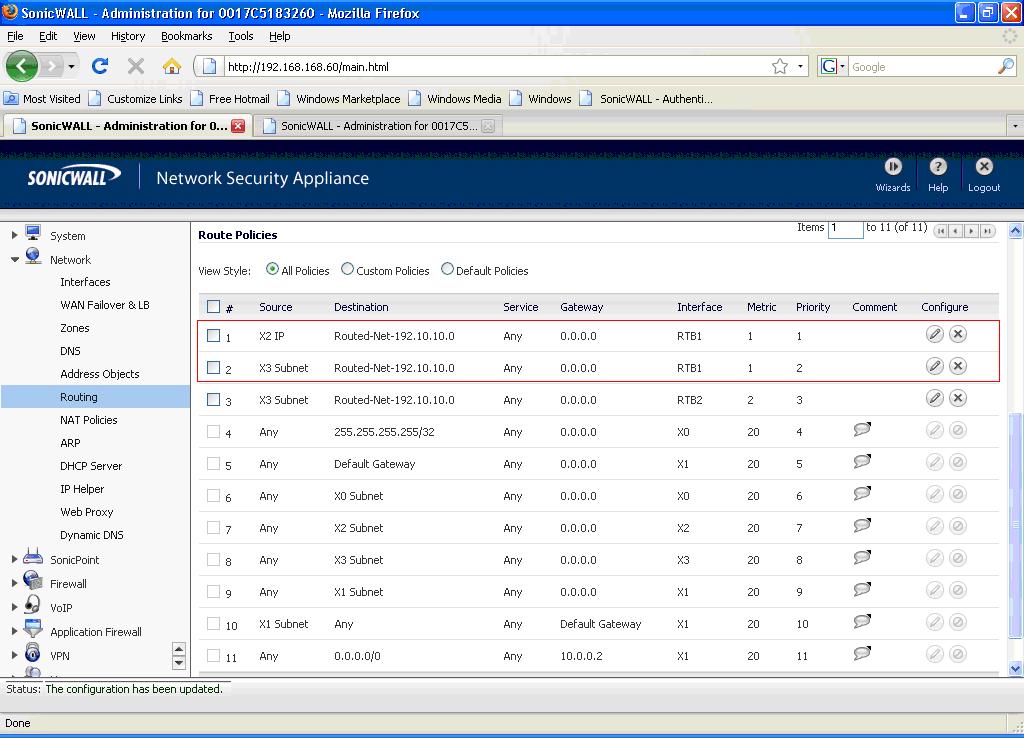
After more than one tunnel interface is configured, you can add multiple overlapping static
routes; each static route uses a different tunnel interface to route the traffic. This provides routing redundancy for the traffic to reach the destination.
The image below illustrates redundant static routes for a network (Routes 2 & 3):

The drop tunnel interface is a pre-configured tunnel interface. This interface provides added
security for traffic. An example of this would be if a static route bind interface is deemed the drop tunnel interface, then all the traffic for that route is dropped and not forwarded in clear. If a static route bind to tunnel interface is defined for traffic (source/destination/service), and it is desired that traffic should not be forwarded in the clear if the tunnel interface is down, it is recommended to configure a static route bind to drop tunnel interface for the same network traffic. As a result, if the tunnel interface is down, traffic will be dropped due to the drop tunnel interface static route.
To add a static route for drop tunnel interface, navigate to
Network
>Routing
>Routing
Policies
. Click the Add
button. Similar to configuring a static route for a tunnel interface, configure the values for Source, Destination, and Service Objects. Under Interface, select “Drop_tunnelIf.”

Once added, the route is enabled and displayed in the Route Polices.

When adding VPN Policies, SonicOS Enhanced auto-creates non-editable Access Rules to
allow the traffic to traverse the appropriate zones. Consider the following VPN Policy, where the Local Network is set to Firewalled Subnets (in this case comprising the LAN and DMZ) and the Destination Network is set to Subnet 192.168.169.0.
While this is generally a tremendous convenience, there are some instances where is might be
preferable to suppress the auto-creation of Access Rules in support of a VPN Policy. One such instance would be the case of a large hub-and-spoke VPN deployment where all the spoke site are addresses using address spaces that can easily be supernetted. For example, assume we wanted to provide access to/from the LAN and DMZ at the hub site to one subnet at each of 2,000 remote sites, addressed as follows:
remoteSubnet0=Network 10.0.0.0/24 (mask 255.255.255.0, range 10.0.0.0-10.0.0.255)
remoteSubnet1=Network 10.0.1.0/24 (mask 255.255.255.0, range 10.0.1.0-10.0.1.255)
remoteSubnet2=Network 10.0.2.0/24 (mask 255.255.255.0, range 10.0.2.0-10.0.2.255)
remoteSubnet2000=10.7.207.0/24 (mask 255.255.255.0, range 10.7.207.0-10.7.207.255)
Creating VPN Policies for each of these remote sites would result in the requisite 2,000 VPN
Policies, but would also create 8,000 Access Rules (LAN -> VPN, DMZ -> VPN, VPN -> LAN, and VPN -> DMZ for each site). However, all of these Access Rules could easily be handled with just 4 Access Rules to a supernetted or address range representation of the remote sites (More specific allow or deny Access Rules could be added as needed):
remoteSubnetAll=Network 10.0.0.0/13 (mask 255.248.0.0, range 10.0.0.0-10.7.255.255)
or
remoteRangeAll=Range 10.0.0.0-10.7.207.255
To enable this level of aggregation, the
Advanced
tab of the VPN Policy
window page offers the option to Auto-Add Access Rules for VPN Policy
setting. By default, the checkbox is selected, meaning the accompanying Access Rules will be automatically created, as they've always been. By deselecting the checkbox upon creating the VPN Policy, the administrator will have the ability and need to create custom Access Rules for VPN traffic.
 (default 28800)
(default 28800)
 (default 28800)
(default 28800)




![]() Choose local network from list
(select an address object):
Choose local network from list
(select an address object):
![]() Local network obtains IP addresses using DHCP through this VPN Tunnel
Local network obtains IP addresses using DHCP through this VPN Tunnel
![]() Use this VPN Tunnel as default route for all Internet traffic
Use this VPN Tunnel as default route for all Internet traffic
![]() Destination network obtains IP addresses using DHCP through this VPN Tunnel
Destination network obtains IP addresses using DHCP through this VPN Tunnel
![]() Choose destination network from list
(select an address object):
Choose destination network from list
(select an address object):
 (default 28800)
(default 28800)
 (default 28800)
(default 28800)




![]() Choose local network from list
(select an address object):
Choose local network from list
(select an address object):
![]() Local network obtains IP addresses using DHCP through this VPN Tunnel
Local network obtains IP addresses using DHCP through this VPN Tunnel
![]() Use this VPN Tunnel as default route for all Internet traffic
Use this VPN Tunnel as default route for all Internet traffic
![]() Destination network obtains IP addresses using DHCP through this VPN Tunnel
Destination network obtains IP addresses using DHCP through this VPN Tunnel
![]() Choose destination network from list
(select an address object):
Choose destination network from list
(select an address object):


Export button for the certificate.







