Deep Packet Inspection of Secure Socket Layer (DPI-SSL) extends SonicWALL’s Deep Packet
Inspection technology to allow for the inspection of encrypted HTTPS traffic and other SSL-based traffic. The SSL traffic is decrypted transparently, scanned for threats and then re-encrypted and sent along to its destination if no threats or vulnerabilities are found. DPI-SSL provides additional security, application control, and data leakage prevention for analyzing encrypted HTTPS and other SSL-based traffic.
The following security services and features are capable of utilizing DPI-SSL:
DPI-SSL has two main deployment scenarios:
The DPI-SSL feature is available in SonicOS Enhanced 5.6. The following table shows which
platforms support DPI-SSL and the maximum number of concurrent connections on which the appliance can perform DPI-SSL inspection.
The Server DPI-SSL deployment scenario is typically used to inspect HTTPS traffic when
remote clients connect over the WAN to access content located on the SonicWALL security appliance’s LAN. Server DPI-SSL allows the user to configure pairings of an address object and certificate. When the appliance detects SSL connections to the address object, it presents the paired certificate and negotiates SSL with the connecting client.
Afterward, if the pairing defines the server to be 'cleartext' then a standard TCP connection is
made to the server on the original (post NAT remapping) port. If the pairing is not defined to be cleartext, then an SSL connection to the server is negotiated. This allows for end-to-end encryption of the connection.
In this deployment scenario the owner of the SonicWALL UTM owns the certificates and private
keys of the origin content servers. Administrator would have to import server's original certificate onto the UTM appliance and create appropriate server IP address to server certificate mappings in the Server DPI-SSL UI.
The following sections describe how to configure Server DPI-SSL:
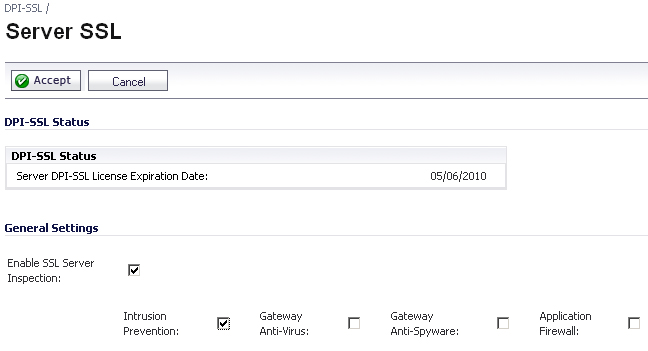
To enable Server DPI-SSL inspection, perform the following steps:
By default, the DPI-SSL applies to all traffic on the appliance when it is enabled. You can
configure an Inclusion/Exclusion list to customize which traffic DPI-SSL inspection will apply to. The Inclusion/Exclusion list provides the ability to specify certain objects, groups, or hostnames. In deployments that are processing a large amount of traffic, it can be useful to exclude trusted sources in order to reduce the CPU impact of DPI-SSL and to prevent the appliance from reaching the maximum number of concurrent DPI-SSL inspected connections.
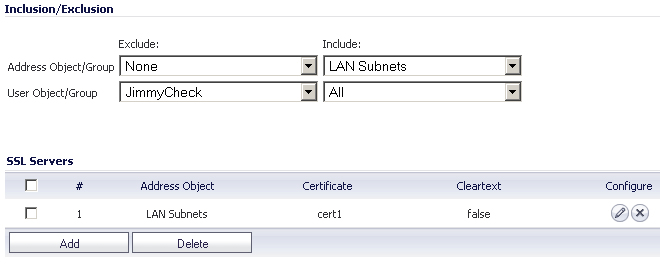
The
Inclusion/Exclusion
section of the Server SSL
page contains two options for specifying the inclusion list:
|
|
•
|
On the
Address Object/Group
line, select an address object or group from the Exclude
pulldown menu to exempt it from DPI-SSL inspection.
|
|
|
•
|
On the
User Object/Group
line, select a user object or group from the Exclude
pulldown menu to exempt it from DPI-SSL inspection.
|
|
|
Note
|
The
Include
pulldown menu can be used to fine tune the specified exclusion list. For example, by selecting the Remote-office-California
address object in the Exclude
pulldown and the Remote-office-Oakland
address object in the Include
pulldown.
|
Server DPI-SSL inspection requires that you specify which certificate will be used to sign traffic
for each server that will have DPI-SSL inspection performed on its traffic. To configure a server-to-certificate pairing, perform the following steps:
|
1.
|
Navigate to the
DPI-SSL > Server SSL
page and scroll down to the SSL Servers
section.
|

|
3.
|
In the
Address Object/Group
pulldown menu, select the address object or group for the server or servers that you want to apply DPI-SSL inspection to.
|
When adding server-to-certificate pairs, a
cleartext
option is available. This option indicates that the portion of the TCP connection between the UTM appliance and the local server will be in the clear without SSL layer, thus allowing SSL processing to be offloaded from the server by the appliance.
Please note that in order for such configuration to work properly, a NAT policy needs to be
created on the Network > NAT Policies
page to map traffic destined for the offload server from an SSL port to a non-SSL port. For example, in case of HTTPS traffic being used with SSL offloading, an inbound NAT policy remapping traffic from port 443 to port 80 needs to be created in order for things to work properly.
