Hardware_Failover_haConfig1
This chapter describes how to configure and manage the High Availability feature on SonicWALL security appliances. It contains the following sections:
High Availability allows two identical SonicWALL security appliances running SonicOS Enhanced to be configured to provide a reliable, continuous connection to the public Internet.One SonicWALL device is configured as the Primary unit, and an identical SonicWALL device is configured as the Backup unit. In the event of the failure of the Primary SonicWALL, the Backup SonicWALL takes over to secure a reliable connection between the protected network and the Internet. Two appliances configured in this way are also known as a High Availability Pair (HA Pair).
High Availability provides a way to share SonicWALL licenses between two SonicWALL security appliances when one is acting as a high availability system for the other. To use this feature, you must register the SonicWALL appliances on MySonicWALL as Associated Products. Both appliances must be the same SonicWALL model.
High Availability provides the following benefits:
Increased network reliability – In a High Availability configuration, the Backup appliance assumes all network responsibilities when the Primary unit fails, ensuring a reliable connection between the protected network and the Internet.
Cost-effectiveness – High Availability is a cost-effective option for deployments that provide high availability by using redundant SonicWALL security appliances. You do not need to purchase a second set of licenses for the Backup unit in a High Availability Pair.
Virtual MAC for reduced convergence time after failover – The Virtual MAC address setting allows the HA Pair to share the same MAC address, which dramatically reduces convergence time following a failover. Convergence time is the amount of time it takes for the devices in a network to adapt their routing tables to the changes introduced by high availability. By default, the Virtual MAC address is provided by the SonicWALL firmware and is different from the physical MAC address of either the Primary or Backup appliances.
High Availability requires one SonicWALL device configured as the Primary SonicWALL, and an identical SonicWALL device configured as the Backup SonicWALL. During normal operation, the Primary SonicWALL is in an Active state and the Backup SonicWALL in an Idle state. If the Primary device loses connectivity, the Backup SonicWALL transitions to Active mode and assumes the configuration and role of Primary, including the interface IP addresses of the configured interfaces. After a failover to the Backup appliance, all the pre-existing network connections must be re-established, including the VPN tunnels that must be re-negotiated.
The failover applies to loss of functionality or network-layer connectivity on the Primary SonicWALL. The failover to the Backup SonicWALL occurs when critical services are affected, physical (or logical) link failure is detected on monitored interfaces, or when the Primary SonicWALL loses power. The Primary and Backup SonicWALL devices are currently only capable of performing Active/Idle High Availability or Active/Active UTM – complete Active/Active high availability is not supported at present.
For SonicWALL appliances that support PortShield, High Availability requires that PortShield is disabled on all interfaces of both the Primary and Backup appliances prior to configuring the HA Pair. Besides disabling PortShield, SonicWALL security appliance configuration is performed on only the Primary SonicWALL, with no need to perform any configuration on the Backup SonicWALL. The Backup SonicWALL maintains a real-time mirrored configuration of the Primary SonicWALL via an Ethernet link between the designated HA ports of the appliances. If the firmware configuration becomes corrupted on the Primary SonicWALL, the Backup SonicWALL automatically refreshes the Primary SonicWALL with the last-known-good copy of the configuration preferences.
There are two types of synchronization for all configuration settings: incremental and complete. If the timestamps are in sync and a change is made on the Active unit, an incremental synchronization is pushed to the Idle unit. If the timestamps are out of sync and the Idle unit is available, a complete synchronization is pushed to the Idle unit. When incremental synchronization fails, a complete synchronization is automatically attempted.
Primary - Describes the principal hardware unit itself. The Primary identifier is a manual designation, and is not subject to conditional changes. Under normal operating conditions, the Primary hardware unit operates in an Active role.
Backup - Describes the subordinate hardware unit itself. The Backup identifier is a relational designation, and is assumed by a unit when paired with a Primary unit. Under normal operating conditions, the Backup unit operates in an Idle mode. Upon failure of the Primary unit, the Backup unit will assume the Active role.
Active - Describes the operative condition of a hardware unit. The Active identifier is a logical role that can be assumed by either a Primary or Backup hardware unit.
Idle - Describes the passive condition of a hardware unit. The Idle identifier is a logical role that can be assumed by either a Primary or Backup hardware unit. The Idle unit assumes the Active role in the event of determinable failure of the Active unit.
Failover - Describes the actual process in which the Idle unit assumes the Active role following a qualified failure of the Active unit. Qualification of failure is achieved by various configurable physical and logical monitoring facilities described throughout the Task List section.
Preempt - Applies to a post-failover condition in which the Primary unit has failed, and the Backup unit has assumed the Active role. Enabling Preempt will cause the Primary unit to seize the Active role from the Backup after the Primary has been restored to a verified operational state.
The Virtual MAC address allows the High Availability pair to share the same MAC address, which dramatically reduces convergence time following a failover. Convergence time is the amount of time it takes for the devices in a network to adapt their routing tables to the changes introduced by high availability.
Without Virtual MAC enabled, the Active and Idle appliances each have their own MAC addresses. Because the appliances are using the same IP address, when a failover occurs, it breaks the mapping between the IP address and MAC address in the ARP cache of all clients and network resources. The Backup appliance must issue an ARP request, announcing the new MAC address/IP address pair. Until this ARP request propagates through the network, traffic intended for the Primary appliance’s MAC address can be lost.
The Virtual MAC address greatly simplifies this process by using the same MAC address for both the Primary and Backup appliances. When a failover occurs, all routes to and from the Primary appliance are still valid for the Backup appliance. All clients and remote sites continue to use the same Virtual MAC address and IP address without interruption.
By default, this Virtual MAC address is provided by the SonicWALL firmware and is different from the physical MAC address of either the Primary or Backup appliances. This eliminates the possibility of configuration errors and ensures the uniqueness of the Virtual MAC address, which prevents possible conflicts. Optionally, you can manually configure the Virtual MAC address on the High Availability > Monitoring page.
The Virtual MAC setting is available even if Stateful High Availability is not licensed. When Virtual MAC is enabled, it is always used even if Stateful Synchronization is not enabled.
Crash Detection
The High Availability feature has a thorough self-diagnostic mechanism for both the Primary and Backup SonicWALL security appliances. The failover to the Backup SonicWALL occurs when critical services are affected, physical (or logical) link detection is detected on monitored interfaces, or when the SonicWALL loses power.
The self-checking mechanism is managed by software diagnostics, which check the complete system integrity of the SonicWALL device. The diagnostics check internal system status, system process status, and network connectivity. There is a weighting mechanism on both sides to decide which side has better connectivity, used to avoid potential failover looping.
Critical internal system processes such as NAT, VPN, and DHCP (among others) are checked in real time. The failing service is isolated as early as possible, and the failover mechanism repairs it automatically.
Stateful High Availability Overview
This section provides an introduction to the Stateful High Availability feature. Stateful High Availability is supported on SonicWALL NSA appliances, but not on SonicWALL TZ series appliances.
This section contains the following subsections:
What is Stateful High Availability?
The original version of SonicOS Enhanced provided a basic High Availability feature where a Backup firewall assumes the interface IP addresses of the configured interfaces when the Primary unit fails. Upon failover, layer 2 broadcasts are issued (ARP) to inform the network that the IP addresses are now owned by the Backup unit. All pre-existing network connections must be rebuilt. For example, Telnet and FTP sessions must be re-established and VPN tunnels must be renegotiated.
Stateful High Availability (SHA) provides dramatically improved failover performance. The Primary and Backup appliances are continuously synchronized so that the Backup can seamlessly assume all network responsibilities if the Primary appliance fails, with no interruptions to existing network connections.
Stateful High Availability provides the following benefits:
Improved reliability - By synchronizing most critical network connection information, Stateful High Availability prevents down time and dropped connections in case of appliance failure.
Faster failover performance - By maintaining continuous synchronization between the Primary and Backup appliances, Stateful High Availability enables the Backup appliance to take over in case of a failure with virtually no down time or loss of network connections.
Minimal impact on CPU performance - Typically less than 1% usage.
Minimal impact on bandwidth - Transmission of synchronization data is throttled so as not interfere with other data.
How Does Stateful High Availability Work?
Stateful High Availability is not load-balancing. It is an active-idle configuration where the Primary appliance handles all traffic. When Stateful High Availability is enabled, the Primary appliance actively communicates with the Backup to update most network connection information. As the Primary appliance creates and updates network connection information (VPN tunnels, active users, connection cache entries, etc.), it immediately informs the Backup appliance. This ensures that the Backup appliance is always ready to transition to the Active state without dropping any connections.
The synchronization traffic is throttled to ensure that it does not interfere with regular network traffic. All configuration changes are performed on the Primary appliance and automatically propagated to the Backup appliance. The High Availability pair uses the same LAN and WAN IP addresses—regardless of which appliance is currently Active.
When using SonicWALL Global Management System (GMS) to manage the appliances, GMS logs into the shared WAN IP address. In case of a failover, GMS administration continues seamlessly, and GMS administrators currently logged into the appliance will not be logged out, however Get and Post commands may result in a timeout with no reply returned.
The following table lists the information that is synchronized and information that is not currently synchronized by Stateful High Availability.
|
Security Services and Stateful High Availability
High Availability pairs share a single set of security services licenses and a single Stateful HA license. These licenses are synchronized between the Active and Idle appliances in the same way that all other information is synchronized between the two appliances. For information on license synchronization, see High Availability License Synchronization Overview and Applying Licenses to SonicWALL Security Appliances.
Stateful High Availability Example
The following figure shows a sample Stateful High Availability network.

In case of a failover, the following sequence of events occurs:
A PC user connects to the network, and the Primary SonicWALL security appliance creates a session for the user.
The Primary appliance synchronizes with the Backup appliance. The Backup now has all of the user’s session information.
The power is unplugged from the Primary appliance and it goes down.
The Backup unit does not receive heartbeat messages from the Primary appliance and switches from Idle to Active mode.
The Backup appliance begins to send gratuitous ARP messages to the LAN and WAN switches using the same Virtual MAC address and IP address as the Primary appliance. No routing updates are necessary for downstream or upstream network devices.
When the PC user attempts to access a Web page, the Backup appliance has all of the user’s session information and is able to continue the user’s session without interruption.
This section provides an introduction to the Active/Active UTM feature. Active/Active UTM requires Stateful High Availability and is supported on SonicWALL E-Class NSA appliances. This section contains the following subsections:
The High Availability feature on versions of SonicOS Enhanced prior to 5.5 uses an active-idle model that requires the active firewall to perform all Unified Threat Management (UTM), firewall, NAT, and other processing, while the idle firewall is not utilized until failover occurs. In an active/active model, both firewalls share the processing.
As a first step towards complete Active/Active High Availability, Deep Packet Inspection (DPI) UTM services are migrated to an Active/Active model, referred to as Active/Active UTM. The following DPI UTM services are affected:
Gateway Anti-Virus (GAV)
Anti-Spyware
Intrusion Protection (IPS)
Application Firewall
When Active/Active UTM is enabled on a Stateful HA pair, these DPI UTM services can be processed concurrently with firewall, NAT, and other modules on both the active and idle firewalls. Processing of all modules other than DPI UTM services is restricted to the active unit.
The benefits of the Active/Active UTM feature include the following:
Both the firewalls in the HA pair are utilized to derive maximum throughput
GAV, IPS, Anti-Spyware, and Application Firewall services are the most processor intensive, and concurrent processing of these services on the idle firewall while the active firewall performs other processing provides the most throughput gain
How Does Active/Active UTM Work?
To use the Active/Active UTM feature, the administrator must configure an additional interface as the HA Data Interface. Certain packet flows on the active unit are selected and offloaded to the idle unit on the HA data interface. DPI UTM is processed on the idle unit and then the results are returned to the active unit over the same interface. The remaining processing is performed on the active unit.
After configuring Stateful High Availability on the appliances in the HA pair, connecting and configuring the HA data interface is the only additional configuration required to enable Active/Active UTM.
High Availability License Synchronization Overview
This section provides an introduction to the SonicWALL High Availability license synchronization feature. This section contains the following subsections:
What is High Availability License Synchronization?
High Availability license synchronization provides a way to share SonicWALL security services, Stateful High Availability, and other licenses between two SonicWALL security appliances when one is acting as a high availability backup for the other. To use this feature, you must register the SonicWALL appliances on mysonicwall.com as Associated Products. Both appliances must be the same SonicWALL model.
High availability license synchronization allows sharing of the SonicOS Enhanced license, the Support subscription, and the security services licenses present on the Primary SonicWALL appliance with the associated Backup appliance. All security services you see on the Security Services > Summary screen are shareable, including Free Trial services. The only licenses that are not shareable are for consulting services, such as the SonicWALL GMS Preventive Maintenance Service. When a hardware failover occurs, the Backup appliance is licensed and ready to take over network security operations.
In SonicOS Enhanced 4.0 and higher, the Stateful High Availability Upgrade is offered on appliance models that support it as an optional licensed feature. On MySonicWALL, only the Primary unit in the HA pair needs to be licensed. With Stateful High Availability the Primary unit actively communicates with the Backup on a per connection and VPN level. As the Primary creates and updates connection cache entries or VPN tunnels, the Backup unit is informed of such changes. The Backup unit remains in a continuously synchronized state so that it can seamlessly assume the network responsibilities upon failure of the Primary unit with no interruption to existing network connections.
High Availability license synchronization is a cost-effective option for deployments that provide high availability by using redundant SonicWALL security appliances. You do not need to purchase a second set of licenses for the Idle unit in a High Availability pair. When the Stateful High Availability Upgrade is licensed, the Backup unit is always synchronized so that there is no interruption to existing network connections if the Primary unit fails.
Stateful and Non-Stateful High Availability Prerequisites
Your network environment must meet the following prerequisites before configuring Stateful High Availability or non-stateful High Availability:
The Primary and Backup appliances must be the same model. Mixing and matching SonicWALLs of different hardware types is not currently supported.
It is strongly recommended that the Primary and Backup appliances run the same version of SonicOS Enhanced firmware; system instability may result if firmware versions are out of sync, and all High Availability features may not function completely. High Availability is only supported on the SonicWALL security appliances running SonicOS Enhanced. It is not supported in any version of SonicOS Standard.
On SonicWALL appliances that support the PortShield feature (SonicWALL TZ series and NSA 240), High Availability can only be enabled if PortShield is disabled on all interfaces of both the Primary and Backup appliances.
Both units must be registered and associated as a High Availability pair on MySonicWALL before physically connecting them.
The WAN virtual IP address and interfaces must use static IP addresses.
Note SonicWALL High Availability cannot be configured using the built-in wireless interface, nor can it be configured using Dynamic WAN interfaces.
Warning SonicWALL High Availability does not support dynamic IP address assignment from your ISP.
Three LAN IP addresses are required:
LAN Virtual IP Address - Configured on the X0 interface of the Primary unit. This is the default gateway for all devices configured on the LAN. Accessing the management interface with this IP address will log you into the appliance that is Active whether it is the Primary unit or Backup unit.
Primary LAN Management IP Address - Configured under High Availability > Monitoring. This is the IP address used for managing the Primary unit over the LAN interface, regardless of the Active or Idle status of the unit.
Backup LAN Management IP Address - Configured under High Availability > Monitoring. This is the IP address used for managing the Backup unit over the LAN interface, regardless of the Active or Idle status of the unit.
At least one WAN IP address is required:
WAN Virtual IP Address - Configured on the X1 Interface of the Primary unit. Accessing the management interface with this IP address will log you into the appliance that is Active whether it is the Primary unit or Backup unit
Primary WAN Management IP Address (Optional) - Configured under High Availability > Monitoring. This is the IP address used for managing the Primary unit over the WAN interface, regardless of the Active or Idle status of the unit. This requires that you have an additional routable IP address available. This is optional, as you can always manage the Active unit with one static WAN IP address.
Backup WAN Management IP Address (Optional) - Configured under High Availability > Monitoring. This is the IP address used for managing the Backup unit over the WAN interface, regardless of the Active or Idle status of the unit. This requires that you have an additional routable IP address available. This is optional, as you can always manage the Active unit with one static WAN IP address.
If using only a single WAN IP, note that the Backup device, when in Idle mode, will not be able to use NTP to synchronize its internal clock.
Note When HA Monitoring/Management IP addresses are configured only on WAN interfaces, they need to be configured on all the WAN interfaces for which a Virtual IP address has been configured.
If you will not be using Primary/Backup WAN Management IP address, make sure each entry field is set to ‘0.0.0.0’ (in the High Availability > Monitoring Page) – the SonicWALL will report an error if the field is left blank.
Note If each SonicWALL has a Primary/Backup WAN Management IP address for remote management, the WAN IP addresses must be in the same subnet. If shifting a previously assigned interface to act as a unique WAN interface, be sure to remove any custom NAT policies that were associated with that interface before configuring it.
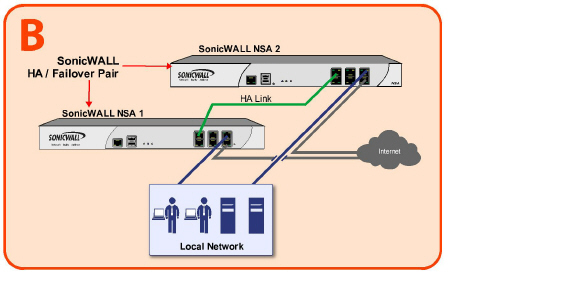
The following figure shows an example of how to connect two SonicWALL security appliances for Stateful High Availability. The units are connected with their designated HA ports.

The LAN (X0) interfaces are connected to a switch on the LAN network. The WAN (X1) interfaces are connected to another switch, which connects to the Internet. The designated high availability interfaces are connected directly to each other using a crossover cable.
Note If you are connecting the Primary and Backup appliances to an Ethernet switch that uses the spanning tree protocol, be aware that it may be necessary to adjust the link activation time on the switch port to which the SonicWALL interfaces connect. For example, on a Cisco Catalyst-series switch, it is necessary to activate spanning tree port fast for each port connecting to the SonicWALL security appliance’s interfaces.
Initial High Availability Setup
Before you begin the configuration of High Availability on the Primary SonicWALL security appliance, perform the following initial setup procedures.
Register and associate the Primary and Backup SonicWALL security appliances as a High Availability pair on MySonicWALL. See Associating Appliances on MySonicWALL for High Availability.
On the back of the Backup SonicWALL security appliance, locate the serial number and write the number down. You need to enter this number in the High Availability > Settings page.
Make sure that the two appliances are running the same SonicOS Enhanced versions.
Make sure Primary SonicWALL and Backup SonicWALL security appliance’s LAN, WAN, and other interfaces are properly configured for seamless failover.
Connect the Primary SonicWALL and Backup SonicWALL appliances with a CAT5 or CAT6-rated crossover cable. The Primary and Backup SonicWALL security appliances must have a dedicated connection between each other for High Availability. SonicWALL recommends cross-connecting the two together using a CAT5/6 crossover Ethernet cable, but a connection using a dedicated 100Mbps hub/switch is also acceptable. The following table shows which interface to use for the various SonicWALL security appliance platforms.
|
Power on the Primary appliance, and then power on the Backup appliance.
Do not make any configuration to the Primary’s High Availability interface; the High Availability programming in an upcoming step takes care of this issue. See Configuring High Availability in SonicOS. When done, disconnect the workstation.
Initial Active/Active UTM Setup
The Active/Active UTM feature requires an additional physical connection between the two appliances in your Stateful HA pair. The connected interface is called the HA Data Interface.
Perform the following steps:
Decide which interface to use for the additional connection between the appliances. The same interface must be selected on each appliance. For example, you could connect X4 on the Primary unit to X4 on the Backup, in which case X4 would be the HA Data Interface.
In the SonicOS Enhanced management interface, navigate to the Network > Interfaces page and ensure that the Zone is Unassigned for the intended HA Data Interface.
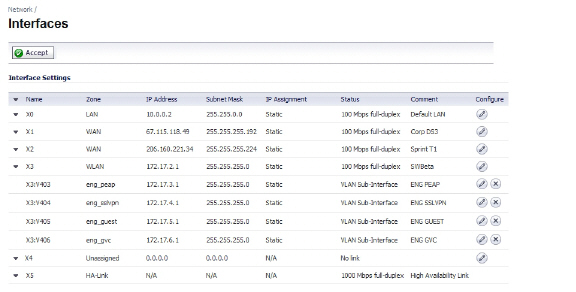
Using a standard Ethernet cable, connect the two interfaces directly to each other.
Associating Appliances on MySonicWALL for High Availability
This section describes how to associate two SonicWALL appliances as a High Availability Pair on mysonicwall.com, and shows an example high availability configuration on SonicOS Enhanced.
You can associate two SonicWALL security appliances as HA Primary and HA Secondary on MySonicWALL. Note that the Backup appliance of your High Availability Pair is referred to as the HA Secondary unit on MySonicWALL. After the appliances are associated as an HA Pair, they can share licenses.
You need only purchase a single set of licenses for the HA Primary appliance. The licenses are shared with the Backup unit. This includes the SonicOS Enhanced license, the Support subscription, and the security services licenses. The only licenses that are not shareable are for consulting services, such as the SonicWALL GMS Preventive Maintenance Service.
It is not required that the Primary and Backup appliances have the same security services enabled. The security services settings will be automatically updated as part of the initial synchronization of settings. License synchronization is used so that the Backup appliance can maintain the same level of network protection provided before the failover.
To use Stateful High Availability on SonicWALL NSA appliances, you must purchase a Stateful High Availability Upgrade license for the Primary unit. Stateful High Availability is a licensed service that must be activated for the Primary appliance on mysonicwall.com. The license is shared with the Backup unit.
License synchronization is used in a high availability deployment so that the Backup appliance can maintain the same level of network protection provided before the failover. To enable high availability, you can use the SonicOS management interface to configure your two appliances as a High Availability pair in Active/Idle mode.
MySonicWALL provides several methods of associating the two appliances. You can start by registering a new appliance, and then choosing an already-registered unit to associate it with. Or, you can associate two units that are both already registered. Or, you can start the process by selecting a registered unit and adding a new appliance with which to associate it.
Note Even if you first register your appliances on MySonicWALL, you must individually register both the Primary and the Backup appliances from the SonicOS management interface while logged into the individual management IP address of each appliance. This allows the Backup unit to synchronize with the SonicWALL license server and share licenses with the associated Primary appliance. When Internet access is restricted, you can manually apply the shared licenses to both appliances. See Applying Licenses to SonicWALL Security Appliances for both procedures.
Configuration Procedures on MySonicWALL
You can associate a SonicWALL security appliance with another appliance of the same model when you first register it, or at any time after both appliances are already registered on MySonicWALL. Procedures for different scenarios are provided in the following sections:
Note You can remove an appliance from an association at any time.
Associating an Appliance at First Registration
To register a new SonicWALL security appliance and associate it as a Backup unit to an existing Primary unit so that it can use High Availability license synchronization, perform the following steps:
Login to MySonicWALL.
On the main page, in the left pane, in the text box under Quick Register, type the appliance serial number and then press Enter or click the arrow button.
On the My Products page, under Add New Product, type the friendly name for the appliance and the authentication code into the appropriate text boxes, and then click Register.
On the Product Survey page, optionally fill in the requested information and then click Continue.
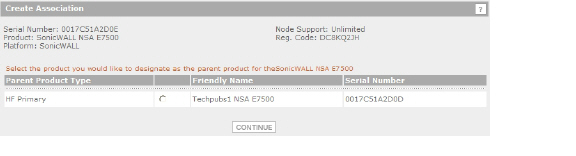
On the Create Association Page, click the radio button for the SonicWALL appliance that you want to act as the parent, or Primary, unit in the High Availability pair. You can skip this step if you want your new appliance to be a Primary unit itself.
The screen displays only units that are not already Backup units for other appliances.
Do one of the following:
To make this appliance a Primary unit, click Continue without clicking a radio button.
If one appliance is available as the parent product (Primary unit), click the radio button to select it, and then click Continue.
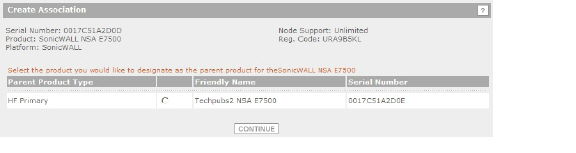
If multiple appliances are available for the parent product, click the radio button for the one you want, and then click Continue.
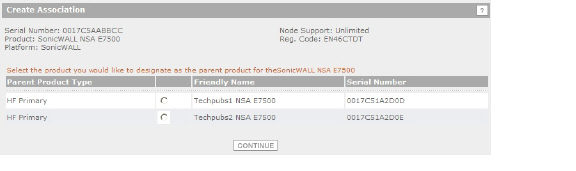
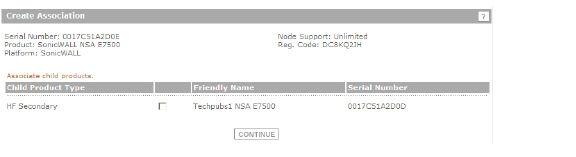
If you clicked Continue without selecting a choice for HA Primary in the preceding step, click the radio button under Child Product Type to select a choice for HA Secondary (Backup unit), and then click Continue. Your new appliance will be the HA Primary unit for the device that you select.
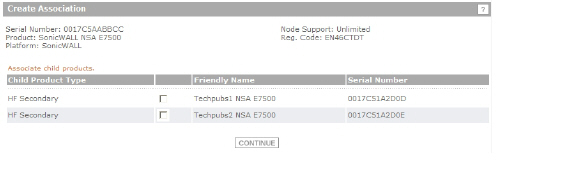
On the next screen, you can verify that your product registered successfully and, at the bottom under Parent Product, verify the correct appliance and serial number for the parent (or child, if you chose that option).

You can click the Serial Number link for the parent product to display the Service Management - Associated Products page and verify that the newly registered appliance is listed as a child product associated with this parent.

You can click HA Secondary to display the My Product - Associated Products page for the child/secondary/Backup unit. Note that you can also change the associated product (parent) for this child on this page.
Associating Pre-Registered Appliances
To associate two already-registered SonicWALL security appliances so that they can use High Availability license synchronization, perform the following steps:
Login to MySonicWALL.
On the main page under Most Recently Registered Products, click View all registered products.
On the My Products page, under Registered Products, scroll down to find the appliance that you want to use as the parent, or Primary, unit. Click the product name or serial number.
On the Service Management - Associated Products page, scroll down to the Associated Products section.
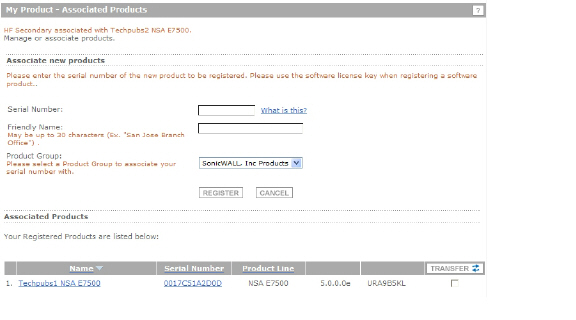
Under Associated Products, click HA Secondary.
On the My Product - Associated Products page, in the text boxes under Associate New Products, type the serial number and the friendly name of the appliance that you want to associate as the child/secondary/Backup unit.
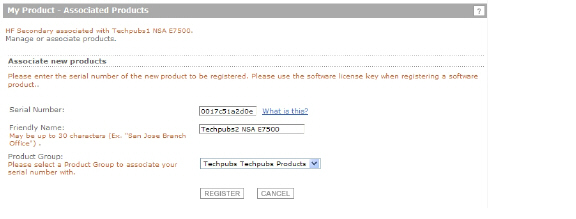
Click Register.
Associating a New Unit to a Pre-Registered Appliance
This section describes how to add a new appliance from the My Product - Associated Products page of an already-registered SonicWALL security appliance, and associate the two appliances so that they can use High Availability license synchronization. You can add a new secondary (Backup) unit to an existing Primary unit, or add a new Primary unit to an existing secondary unit. To use this method, perform the following steps:
Login to MySonicWALL.
On the main page under Most Recently Registered Products, click View all registered products.
On the My Products page, under Registered Products, scroll down to find the appliance that you want to use as the existing unit. You can choose any supported appliance on the list, whether it is already an HA Primary or an HA Secondary, or neither. Click the product name or serial number.
On the Service Management - Associated Products page, scroll down to the Associated Products section.
Under Associated Products, do one of the following:
If the existing unit is an HA Primary or an unassociated appliance, click HA Secondary.
If the existing unit is an HA Secondary appliance, click HA Primary.
On the My Product - Associated Products page, in the text boxes under Associate New Products, type the serial number and the friendly name of the new appliance that you want to register as the associated unit.
Click Register.
On the Product Survey page, optionally fill in the requested information and then click Continue.
On the Create Association page, if multiple qualifying existing appliances are displayed, click the radio button to select the unit with which you want to associate the new unit. If you selected an existing HA Primary unit or unassociated unit in Step 3, the choices here will all be HA Primary. If you selected an existing HA Secondary unit in Step 3, the available selections here will be HA Secondary units.
Click Continue.
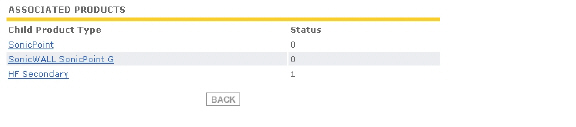
On the Service Management - Associated Products page, confirm at the top that the registration was successful, then scroll to the bottom to see the Associated Products and click either HA Primary or HA Secondary to display the unit(s) that are now associated with your newly registered appliance.
For example, continuing the example shown above, you would see the following:
You can remove the association between two SonicWALL security appliances on MySonicWALL at any time. You might need to remove an existing HA association if you replace an appliance or reconfigure your network. For example, if one of your SonicWALL security appliances fails, you will need to replace it. Or, you might need to switch the HA Primary appliance with the Backup, or HA Secondary, unit after a network reconfiguration. In either case, you must first remove the existing HA association and then create a new association that uses a new appliance or changes the parent-child relationship of the two units.
See Replacing a SonicWALL Security Appliance. To remove the association between two registered SonicWALL security appliances, perform the following steps:
Login to MySonicWALL.
In the left navigation bar, click My Products.
On the My Products page, under Registered Products, scroll down to find the secondary appliance from which you want to remove associations. Click the product name or serial number.
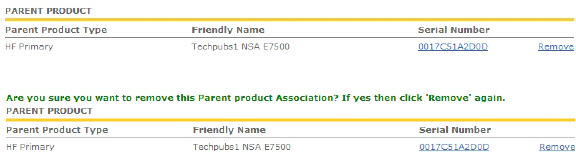
On the Service Management - Associated Products page, scroll down to the Parent Product section, just above the Associated Products section.
Under Parent Product, to remove the association for this appliance, click Remove, wait for the page to reload, scroll down, and then click Remove again.
Replacing a SonicWALL Security Appliance
If your SonicWALL security appliance has a hardware failure while still under warranty, SonicWALL will replace it. In this case, you need to remove the HA association containing the failed appliance in MySonicWALL, and add a new HA association that includes the replacement. If you contact SonicWALL Technical Support to arrange the replacement (known as an RMA), Support will often take care of this for you.
After replacing the failed appliance in your equipment rack with the new unit, you can update MySonicWALL and your SonicOS configuration.
Replacing a failed HA Primary unit is slightly different than replacing an HA Secondary unit. Both procedures are provided in the following sections:
To replace an HA Primary unit, perform the following steps:
In the SonicOS management interface of the remaining SonicWALL security appliance (the Backup unit), on the High Availability screen, uncheck Enable High Availability to disable it.
Clear the Backup SonicWALL Serial Number text box.
Check Enable High Availability.
The old Backup unit now becomes the Primary unit. Its serial number is automatically displayed in the Primary SonicWALL Serial Number text box.
Type the serial number for the replacement unit into the Backup SonicWALL Serial Number text box.
Click Synchronize Settings.
On MySonicWALL, remove the old HA association.See Removing an HA Association.
On MySonicWALL, register the replacement Sonicwall security appliance and create an HA association with the new Primary (original Backup) unit as the HA Primary, and the replacement unit as the HA Secondary. See Associating an Appliance at First Registration.
Contact SonicWALL Technical Support to transfer the security services licenses from the former HA Pair to the new HA Pair.
This step is required when the HA Primary unit has failed, because the licenses are linked to the Primary unit in an HA Pair.
Replacing an HA Secondary Unit
To replace an HA Secondary unit, perform the following steps:
On MySonicWALL, remove the old HA association. See Removing an HA Association.
On MySonicWALL, register the replacement SonicWALL security appliance and create an HA association with the original HA Primary, using the replacement unit as the HA Secondary. See Associating an Appliance at First Registration.
Configuring High Availability in SonicOS
To configure High Availability, you must configure High Availability in the SonicOS management interface using the two SonicWALL appliances associated on MySonicWALL. For information about associating two appliances, see Associating Appliances on MySonicWALL for High Availability.
Before configuring Active/Active UTM, you must configure two SonicWALL security appliances as a Stateful High Availability pair and enable Stateful Synchronization in the SonicOS management interface.
On SonicWALL appliances that support the PortShield feature (SonicWALL TZ series and NSA 240), High Availability can only be enabled if PortShield is disabled on all interfaces of both the Primary and Backup appliances.
You can disable PortShield either by using the PortShield Wizard, or manually from the Network > PortShield Groups page.
Refer to the following sections:
Disabling PortShield with the PortShield Wizard
On SonicWALL appliances that support the PortShield feature, High Availability can only be enabled if PortShield is disabled on all interfaces of both the Primary and Backup appliances. Perform the procedure for each of the appliances while logged into its individual management IP address.To use the PortShield Wizard to disable PortShield on each SonicWALL, perform the following steps:
On one appliance of the planned HA Pair, click the Wizards button at the top right of the management interface.
In the Welcome screen, select PortShield Interface Wizard, and then click Next.
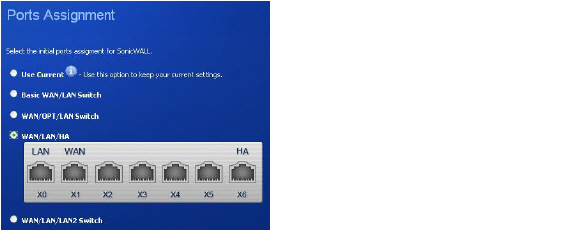
In the Ports Assignment screen, select WAN/LAN/HA, and then click Next.
In the SonicWALL Configuration Summary screen, click Apply.
In the PortShield Wizard Complete screen, click Close.
Log into the management interface of the other appliance in the HA Pair and repeat this procedure.
On SonicWALL appliances that support the PortShield feature, High Availability can only be enabled if PortShield is disabled on all interfaces of both the Primary and Backup appliances. Perform the procedure for each of the appliances while logged into its individual management IP address.
To manually disable PortShield on each SonicWALL, perform the following steps:
On one appliance of the planned HA Pair, navigate to the Network > PortShield Groups page.
Click the Select All link at the top of the page.
Click the Configure button.
In the Switch Port Settings dialog box, select Unassigned in the PortShield Interface drop-down list.
Click OK.
The Network > PortShield Groups page displays the interfaces as unassigned.
The configuration tasks on the High Availability > Settings page are performed on the Primary unit and then are automatically synchronized to the Backup.To configure the settings on the High Availability > Settings page:
Login as an administrator to the SonicOS user interface on the Primary SonicWALL.
In the left navigation pane, navigate to High Availability > Settings. See Verifying High Availability Status for a description of the fields listed in the High Availability Status table.
Select the Enable High Availability checkbox.
Under SonicWALL Address Settings, type in the serial number for the Backup SonicWALL appliance. You can find the serial number on the back of the SonicWALL security appliance, or in the System > Status screen of the Backup unit. The serial number for the Primary SonicWALL is automatically populated.
When finished with all High Availability configuration, click Accept. All settings will be synchronized to the Idle unit, and the Idle unit will reboot.